Phishing:
Definition, Types of Attacks,
and Examples
What is Phishing?
Phishing is a homophone of fishing which is similar to the idea behind fishing, and both terms are homophones of the English language. Fishing is the act, occupation, or sport of catching fish. Phishing, on the other hand, is the act of sending email that falsely claims to be from a legitimate organisation.
This is usually combined with a threat or request for information; for example, that an account will close, a balance is due, or information is missing from an account. The email will ask the recipient to supply confidential information such as bank account details, PINs or passwords; these details are then used by the owners of the website to conduct fraud.
Fishing and Phishing has one thing in common, i.e. BAIT. Fishing bait is any substance used to attract and catch fish, whereas phishing bait (an online and physical social engineering attack that promises the victim a reward) include deceptive emails, websites, and text messages to steal information.
Phishing attacks are one of the most common security challenges that both individuals and companies face in keeping their information secure. Whether it is getting access to passwords, credit cards, or other sensitive information, hackers are using email, social media, phone calls, and any form of communication they can to steal valuable data. Businesses, of course, are a particularly worthwhile target.
Common phishing attacks against businesses:
 Company Impersonation
Company Impersonation
One of the most common forms of phishing is where attackers impersonate your brand. This is typically done with an email connected to a domain very similar to the target company. It is also a difficult attack for companies to look out for due to the fact that you won’t know until someone falls for it or alerts you.
“Spear” Phishing
This type of scheme involves using a fake company name (impersonation) but also key details about the target. Much like in sales, a rep finds the name, position, and other personalization and includes that in a pitch email. Attackers find those same tokens and use it to compel more victims into their trap. It is an especially dangerous ploy.
Email Takeovers
All members of your executive and management team are vulnerable. If a phishing scammer acquires the email credentials of high-profile leadership, it is likely they will target anyone they can be using that very email address. Potential targets would be; colleagues, team members and even customers (if they have already obtained this information via hack).
Phone Phishing
Using Voice over Internet Protocol (VoIP) technology, scammers, again, impersonate companies. This technique also employs other types of phishing, including using personal details about targets and impersonating individuals of the company (e.g. the CEO) in order to get a higher take on the overall scam.
Examples of Phishing
Anecdote of an actual incident confirming the fact that in any organisation in relation to phishing, the weakest link is humans:
Picture a classroom filled with junior and senior executives attending a cybersecurity awareness presentation about Phishing Scams. 10 minutes before closing, presenter reminded the audience to remember never ever to click on or open any suspicious URLs or links received from Emails, SMS’ or any messaging platforms such as WhatsApp, Telegram, Signal, LINE, Snapchat, etc and social media platforms the likes of Facebook, Instagram, Twitter and/or LinkedIn.
All attendees were looking intelligently attentive and nodded, indicating they understood. Class ended.
The presenter emailed to all attendees a fake phishing email with a fake URL promising a gift voucher. The fake link was actually a script noting the clicker’s name and email address to record the email recipients who clicked on the link. Recipients were not bothered, nor were they suspicious of the unknown email sender. Lo and behold, over 50% of the attendees clicked on the link gullibly.
Gullible fools a dime a dozen, one born every minute. Thus, the idiom from the movie Forrest Gump, holds true ie. “Stupid is as stupid does”, meaning that a person should be judged by his actions, not his appearance. Similarly, an intelligent person who does stupid things is still stupid. You are what you do.
Here are recent news on phishing scams:
Nearly 470 people lose at least S$8.5mil in phishing scams involving OCBC Bank
Young couple in SG lost S$120,000 in fake text message scam targeting bank customers | The Star
SMS Phishing
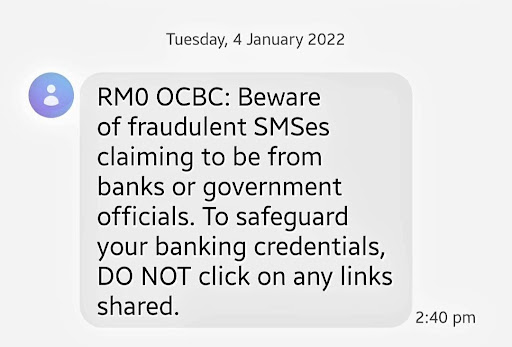
Below is a genuine SMS from a bank, OCBC, reminding recipient about fraudulent SMS’es claiming to be from the bank:
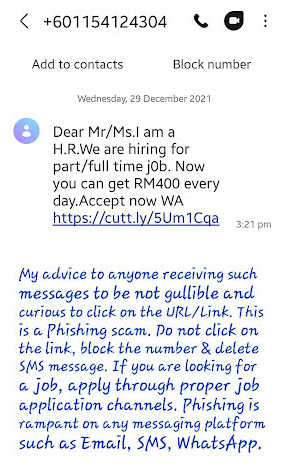
Below is a genuine example of a SMS Phishing:
Email Phishing
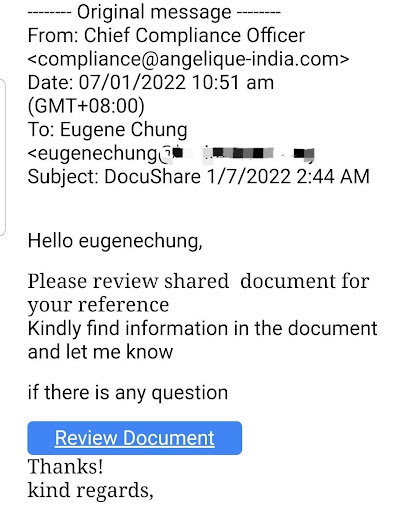
Below is a genuine Email Phishing:
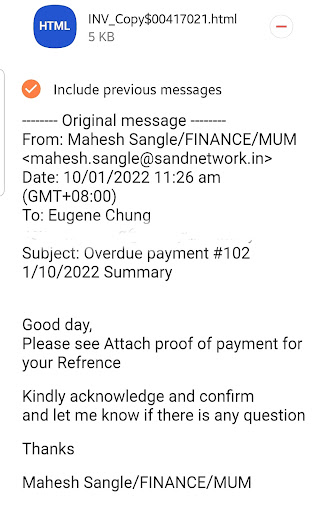
Here’s another genuine email phishing:
In conclusion, computer systems and applications can be protected but have you heard of the Dunning-Kruger effect? It says that while the competent are often plagued with doubt, the incompetent tend to be blissfully sure of their excellence or to put it more bluntly, stupid or incompetent people are often too stupid or incompetent to understand exactly how stupid and incompetent they are. They think they’re awesome.
The Dunning-Kruger Effect excerpt above was extracted from this article:
How Not to Be Stupid, According to a Top Stupidity Researcher
In summary, 5 common types of Phishing:
Catch When Expert Meets Expert by Eugene Chung articles every bi-weekly Tuesday. Don’t forget to subscribe to stay connected. You are also encouraged to ask questions and seek advice from him.
Share this post
Related Posts

Cybersecurity: Achieving the ‘Hole-in-One’ of Digital Defence
- 07 Nov 2023
- By:Bernadetta Septarini
- Category: When Experts Meet Experts (WEME)
Discover the connection between cybersecurity and sports with Tony Smith, Regional VP at WithSecure. Let’s achieve the ‘Hole-in-One’ of Digital Defense.

Beware of Scare Software aka Scareware
- 21 Nov 2022
- By:Eugene Chung
- Category: When Experts Meet Experts (WEME)
What is Scare Software or Scareware? Learn more about this Social Engineering technique that aimed to scare the victim with ArmourZero mentor Eugene Chung.

Job Hunting Tips for IT Graduates
- 14 Nov 2022
- By:Ts. Saiful Bakhtiar Osman
- Category: When Experts Meet Experts (WEME)
The job market is tough and competitive. Learn some tips on how to do job hunting for IT graduates from ArmourZero’s mentor and expert Ts. Saiful Bakhtiar.

Tips to Successfully Sell a Credible Cybersecurity Solution
- 07 Nov 2022
- By:Eugene Chung
- Category: When Experts Meet Experts (WEME)
How do Cybersecurity sales convince prospects to trust their services and/or products? Learn more about it from ArmourZero’s mentor and expert Eugene Chung.



