Check Your Business
Email Security Level
Protection should make us feel at ease, especially if we use Microsoft 365 and Google Workspace for our work.
Get a FREE 14-days email assessment to check your organisation’s security level.
Powered by:
The Award-Winning Email Security Solution

All-in-one Email Security
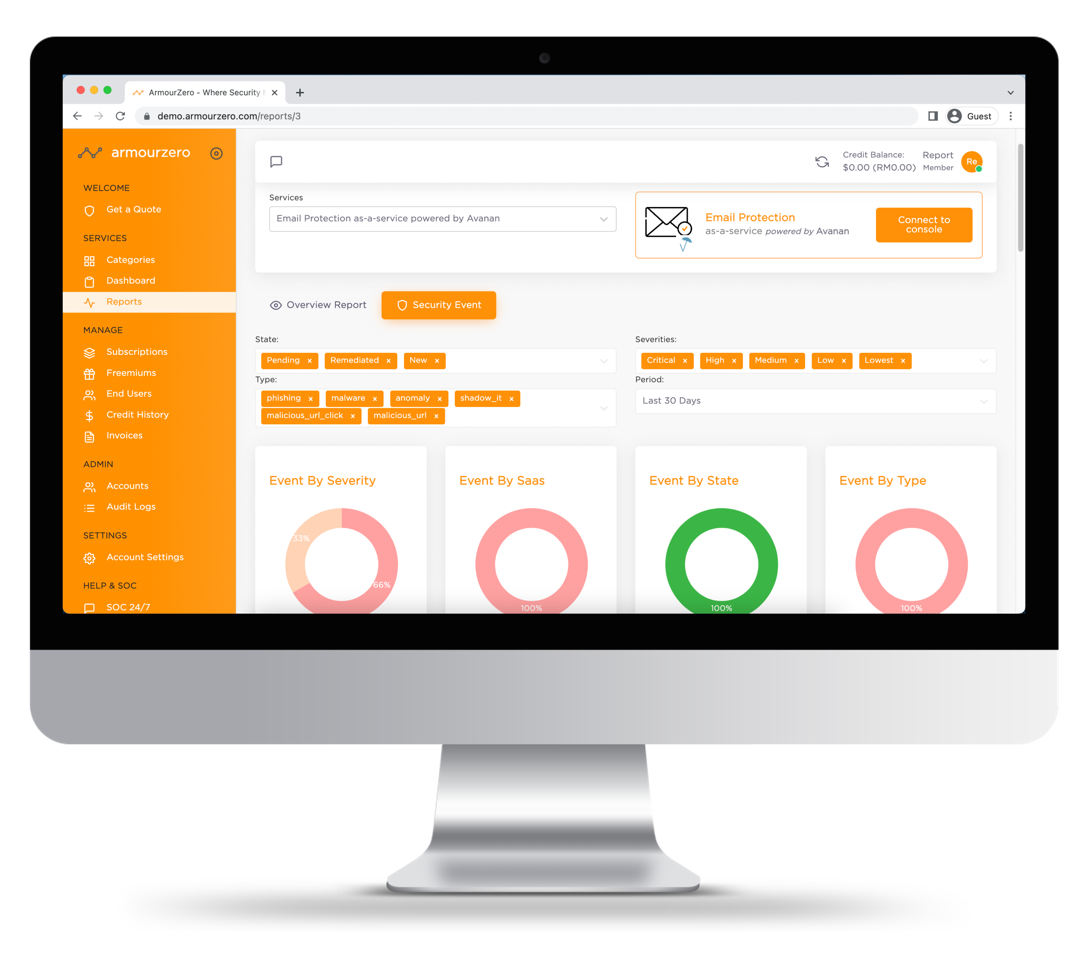
- API integrated with Microsoft 365 and Google Workspace with one-click setup
- 14 days of historical emails (upon activation)
- 14 days real-time emails scan and report
- The Assessment also covers scanning of infected files in Microsoft SharePoint, OneDrive, Teams, and Google Drive
- Ability to cover inbound, outbound, and even internal emails
- Guarantee no network changes including MX record or email redirection
My 14 Days Assessment Journey
Day 1
- Assessment introduction
- One-click setup and integration to Microsoft 365 or Google Workspace
- Immediate scanning for inbound, outbound & internal email threats
Day 4 - 7
- Follow-up session (30 minutes)
- Dashboard / Reporting walk-thru
- Question & Answer Session
Day 14
- Assessment Wrap-up
- Discussion
- Report compilation

Protecting Your Business Has
Never Been This Easy
Catch What You Missed
Modern phishing and BEC attacks use inside information to bypass traditional defenses. Here, our service deploys internally, capturing context out of the reach of traditional gateways, and blocks block messages before they reach the inbox. Before they spread.

Easy Deployment
In just one click, API integrated with Microsoft 365 and no network changes including MX record or email redirection. The algorithm learns from your environment, quarantines existing threats, and identifies phishing, malware, data leakage, and account compromise immediately.

All Around Assessments
Besides Microsoft’s email, this assessment covers scanning of infected files in Microsoft SharePoint, OneDrive, and Teams. Also, we cover inbound, outbound and internal emails. If you have Microsoft 365 anti-phishing or other anti-spam solution, this assessment can serve as validation of your current solution’s status.

Monitoring and Report
During the assessment, you can receive 14 days historical emails (upon activation) and real-time emails scan. Assessment only in monitoring mode with no security policies applied. After 14 days, you will not only receive report about phishing and malware attack detection but also top attacked target users.

