Beware of
Business Email Compromise
(BEC) Scams

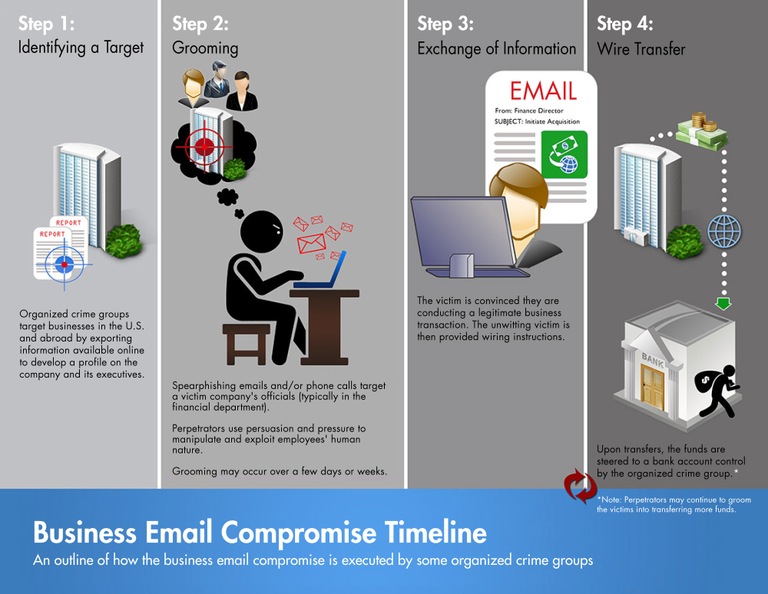
Business Email Compromise (BEC) is an email-based scam, a spear-phishing attack to be exact, that has the objective of tricking employees into taking harmful action by sending money to the attacker. BEC is a classic example of cybercrime because it does not require any sophisticated skill such as hacking a system but becomes one of the most damaging and expensive types of scam that causes victims huge monetary loss each year.
As more companies shift their operations online, cybercriminals have more opportunities to launch BEC attacks. Moreover, it is now very easy to get corporate or public email accounts of executives or high-level employees in finance, HR, or purchasing, so the probability of success increases.
Types of Business Email Compromise (BEC) Scams
According to Interpol’s ASEAN Cyber Threats Assessment 2021, the number one key cybercrime trend and threat in ASEAN is Business Email Compromise (BEC), followed by Phishing, Ransomware, E-commerce Data Interception, Crimeware-as-a-Service, Cyber Scams, and Cryptojacking. In a BEC scam, the attackers pose as someone the recipient should trust, such as a colleague, boss, or vendor. Based on the FBI, there are 5 types of BEC attacks:
1. False Invoice Scam
The tactic is the attacker pretends to be the supplier requesting fund transfer for invoice payments to a bank account owned by them. Most of the targets are companies with foreign suppliers.
2. CEO Fraud
The attackers pretend to be the CEO or any high-level executive and send an email to employees in finance requesting them to transfer money to their account or send sensitive information to them.
3. Account Compromise
Cybercriminals hacked and used an executive email account to request invoice payments to vendors listed in their email contacts. The payment of course was sent to a fake bank account.
4. Attorney Impersonation
Attackers pretend to be a lawyer or someone from the law firm that is in charge of crucial and confidential matters. Normally, such bogus requests are done through email or phone, and during the end of the business day
5. Data Theft
Employees under HR and bookkeeping are targeted to obtain personally identifiable information (PII) or tax statements of employees and executives. That data can be used for future attacks.
In addition, these attackers carefully research and closely monitor the potential target of all types of organisations, from financial to healthcare, educational, also governments, non-governmental agencies, and nonprofits. Therefore, BEC scams rely on impersonation and other social engineering techniques to trick people interacting on the attackers’ behalf. Due to this nature, BEC attacks are difficult to detect because it does not use malware or malicious URLs that can be analysed with standard cyber defences.
How Serious is BEC Attack?
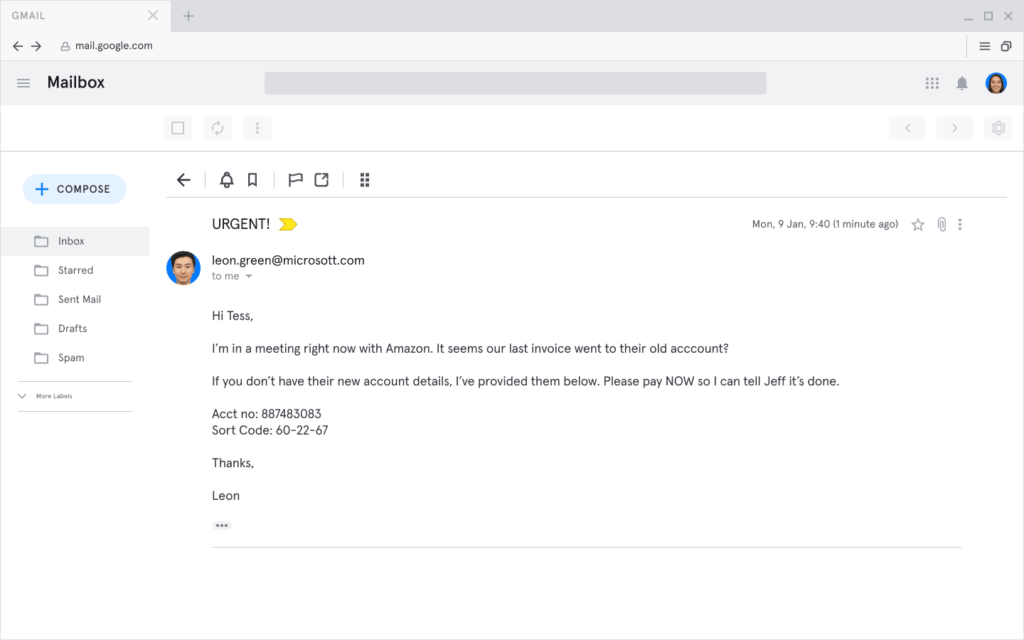
One of the BEC examples is the impersonation of a colleague. (Source: Tessian.com)
BEC was not considered a global threat until 2013 when the IC3 (Internet Crime Complaint Centre, founded in 2000) received massive complaints and issues about them. It was reported from 2013 to 2014 that the total number of BEC victims in the U.S. and 45 countries are 2,226 with a combined money loss of US$214,972,503.30.
From May 2018 to June 2019, there was a 100% increase in total global fraud from BEC. Since the IC3 started counting, there has been a total money loss of US$26.2 billion with victims from all 50 states in the U.S. and in 177 countries. No wonder the FBI has named BEC a “US$26 billion scam”. In 2020, the IC3 observed an increase in the number of BEC complaints related to the use of identity theft and funds being converted to cryptocurrency.
There are several top BEC cases, such as:
-
Facebook and Google: US$121m BEC scam
It was dubbed the biggest BEC scam of all time. The attacker Evaldas Rimasauskas and associates set up a fake company named “Quanta Computer” (the same name as the real hardware supplier) which sent fake invoices, contracts, and letters, and billed them for millions of dollars in 2013-2015. The documents were legitimate-looking enough that Google and Facebook wired money to accounts.
-
Ubiquiti: US$46.7m vendor fraud
In August 2015, IT company Ubiquiti became the victim of US$46.7 million due to the scammers who impersonated employees at a third-party company (vendor) and targeted Ubiquiti’s finance department.
-
Toyota: US$37 million BEC attack
In 2019, Japan’s Toyota Boshoku Corporation, a supplier of auto parts, was a victim of US$37 million. The attackers tricked and persuaded an executive of the finance department to make a wire transfer.
-
Government of Puerto Rico, 2019-2020
In early 2020, while dealing with the aftermath of the earthquake, the government fell victim to BEC attacks when Ruben Rivera, finance director of Puerto Rico’s Industrial Development Company mistakenly transferred over US$2.6 million to a fraudulent bank account. He had received an email about the changing bank account tied to remittance payments. Fortunately, the money which included public pension funds was frozen by the FBI.
How to prevent Business Email Compromise Scams
BEC scams are hard to stop because it needs internal context to know if the email is legit or not. Several tips from FBI to guard against BEC, such as:
- Don’t click on anything in an unsolicited email or text message asking you to update or verify account information. Look up the company’s phone number on your own (don’t use the one a potential scammer is providing), and call the company to ask if the request is legitimate.
- Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.
- Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.
- Set up two-factor (or multi-factor) authentication on any account that allows it, and never disable it.
- Verify payment and purchase requests in person if possible or by calling the person to make sure it is legitimate. You should verify any change in an account number or payment procedures with the person making the request.
- Be especially wary if the requestor is pressing you to act quickly.
To increase security safety in your company, use cybersecurity solutions that give email protection that leverages internal context, AI, and a trusted reputation network unique to a company and can prevent BEC attacks such as Avanan.
In fact, here’s how Avanan prevents organisations from BEC:
- Machine learning algorithms combine with role-based, contextual analysis of previous conversations to identify threats that Google, Microsoft and external mail gateways miss,
- Deployment-day analysis of one-year’s email conversations to build a trusted reputation network,
- Scanning and quarantine of internal email and files in real-time, protecting against east-west attacks and insider threats,
- AI and machine learning techniques to rapidly adapt to new threats and behaviours,
- Account takeover protection beyond email: login events, configuration changes and end user activities throughout the suite.
ArmourZero provides Email Protection as-a-Service powered by Avanan, the best breed of Email Security Solutions, with only US$6.00/user/month or US$60/user/year we are able to prevent delivery of malicious emails to inbox, protect Microsoft 365 and Google Workspace email, account takeover prevention, etc. Book your demo now.
![]()
Written by:
Fanny Fajarianti (Performance Marketing). Experienced digital marketer in the information technology and services industry.
Share this post
Related Posts

Earth Day: The Connection of Cybersecurity and Sustainability
- 22 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Uncover the link between Earth Day and Cybersecurity, promoting sustainability through data protection and environmental stewardship. Let’s secure a greener future.

What is DevSecOps? Definition & Best Practices for Tech Industries
- 18 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Learn about DevSecOps, principles, and best practices for the tech industry. Integrate security seamlessly into software development and enhance quality.

Safeguarding Your Organisation During the Hari Raya Holiday
- 09 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Protect your organisation from holiday cyberattacks during Hari Raya. Learn more about the risks and best practices for holiday security with ArmourZero.

Cyberattacks: A Growing Threat to Higher Education
- 02 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Universities hold sensitive data but face cyberattack risks in the digital age. Explore the impact of cyberattack and learn how to protect your institution.