Lockbit Ransomware:
Battling Cyber Threats

LockBit ransomware has been implicated in more cyberattacks this year than any other ransomware, making it the most active ransomware in the world. LockBit has been responsible for 124 out of the 380 attacks in August 2023, marking a significant month-over-month increase from the 41 victims the previous month.
While the average ransomware payment is nearly $1 million per incident, LockBit victims pay an average ransom of approximately $85,000, indicating that LockBit targets small-to-medium-sized organisations. While it was once thought to target small-to-medium-sized organisations with relatively low ransom demands, recent reports indicate that LockBit threat actors demanded an astonishing $8 million ransom from a recent Enterprise victim.
Understanding LockBit Ransomware
LockBit ransomware is a significant threat with a history dating back to September 2019 when it first emerged as “ABCD Ransomware” before adopting the name “LockBit.” Since then, it has evolved with various versions and tactics. Here’s a summary of its evolution:
- September 2019: LockBit’s journey begins as “ABCD Ransomware,” later rebranded as “LockBit.”
- June 2021: LockBit 2.0 emerges, introducing the dual-extortion strategy and automatic encryption across Windows domains.
- October 2021: LockBit starts targeting Linux servers, especially ESXi servers, and introduces “StealBit” for encryption.
- June 2022: LockBit 3.0, also known as LockBit Black, appears, featuring a ransomware bug bounty program, new extortion tactics, and payment options using Zcash cryptocurrency. Its code shares similarities with BlackMatter and DarkSide ransomware.
- September 2022: A disgruntled developer leaks LockBit 3.0’s encryptor builder, enabling others to create ransomware kits. This leads to attacks by groups like Bl00dy.
- January 2023: LockBit Green emerges, based on the leaked source code of Conti ransomware.
- April 2023: Reports surface of LockBit ransomware targeting macOS, marking a significant expansion.
LockBit 2.0 Attack Strategy
LockBit 2.0 attacks are infamous for employing a dual-extortion strategy, intended to pressure victims into making two payments as quickly as possible. The urgency stems from the fact that LockBit not only encrypts the data locally, but also infiltrates it to the malware operators even before the ransom demand is issued.
The first payment is required to regain control over the encrypted files, while the second aims to prevent the public exposure of the stolen data. In cases where LockBit operates as a Ransomware-as-a-Service (RaaS), a crucial figure known as the Initial Access Broker (IAB) comes into play. The IAB’s role involves deploying initial-stage malware or gaining unauthorised access to an organisation’s infrastructure. This access is then monetised by selling it to the primary LockBit operator, who proceeds with the second-stage exploitation.
For uncooperative victims or those who refuse to meet ransom demands, LockBit’s menacing response is to publish the victim’s data on its ominous “Leaked Data” site, which resides on the dark web at hxxp[:]//lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion.
LockBit 3.0 Attack Techniques
LockBit 3.0 epitomises a new era of ransomware, blending data destruction, encryption, defacement, and system disruption for maximum impact. Its versatility in targeting various devices and employing advanced techniques elevates it as a significant cybersecurity threat. Now, let’s delve into LockBit 3.0’s key techniques:
- Data Destruction: LockBit 3.0 excels in erasing digital footprints efficiently. It employs the Data Destruction technique, wiping log files and emptying the recycle bin. This not only conceals its tracks but also hinders victim traceability.
- Data Encryption for Impact: LockBit 3.0’s core mission is to disrupt system and network resources. Using the Data Encryption for Impact technique, it encrypts data on target systems. This ruthless encryption renders data inaccessible and paralyses operations, profoundly affecting victims. LockBit affiliates adeptly encrypt various devices, including Windows and Linux systems, as well as VMware instances.
- Internal Defacement: LockBit 3.0 goes beyond destruction and encryption. It executes internal defacement through the Internal Defacement technique, altering the host system’s wallpaper and icons with its branding. This not only insults the victim but also serves as a chilling reminder of the breach.
- Inhibition of System Recovery: Victims often rely on system recovery to restore operations during an attack. LockBit 3.0 is well-prepared to counter these efforts, using the Inhibition of System Recovery technique to delete volume shadow copies on the disk. By eliminating recovery points, it cuts off victims’ escape routes, making recovery an arduous task.
- Service Termination: LockBit 3.0’s ruthless assault extends to terminating critical processes and services with the Service Termination technique. This strategic move disrupts system functionality, intensifying the chaos and compounding the attack’s impact.
LockBit Ransomware Target
LockBit primarily targets Windows computers, although newer versions have been modified to attack specific types of computer setups using Linux. These setups are commonly found in large data centres, such as VMWare ESXi virtual machines.
LockBit often focuses on medium-sized organisations. This preference may be due to their use of a method called Ransomware-as-a-Service (RaaS). This means that someone within the organisation can act as an intermediary, set their own ransom price, and collect the ransom directly.
LockBit Expands to macOS
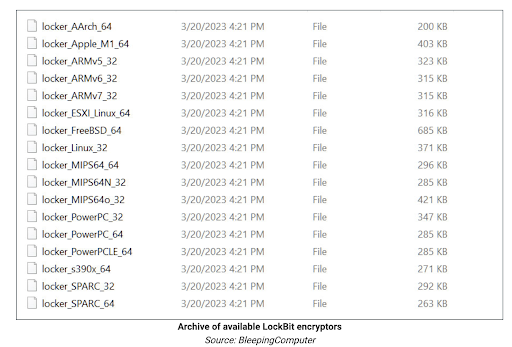
The LockBit ransomware group has introduced encryptors specifically designed for Mac computers, signifying a significant development. This move positions LockBit as potentially the first prominent ransomware operation to target macOS exclusively in 2023.
The existence of these new ransomware encryptors came to light when cybersecurity researcher MalwareHunterTeam discovered a ZIP archive on VirusTotal. This archive contained what appears to be a collection of LockBit encryptors, including newly adapted versions for macOS.
While some samples, like the macOS variant, require additional configuration and lack proper signatures, it’s evident that LockBit is actively experimenting with its ransomware across various platforms. This suggests an imminent expansion of their attack capabilities. This underscores the critical need for robust cybersecurity measures across all platforms and a heightened level of awareness within businesses.
For a detailed technical analysis of the new Mac encryption, refer to Wardle’s report on Objective See.

How Can We Protect Against LockBit Ransomware?
The escalating threat of LockBit Ransomware necessitates a proactive cybersecurity approach. To shield yourself and your organisation from its malevolent reach, consider these recommendations from ArmourZero:
1. Effective Backup Strategy
Foiling a successful LockBit attack requires robust cybersecurity measures and a comprehensive backup strategy, including encrypted offline and offsite backups.
2. Regular Patching
Ensure the security of your systems and software by consistently applying patches. ArmourZero offers Patch Management as a service powered by Automox. Automox is the only cloud-native patching platform that fully automated patch management across Windows, macOS, Linux, and third-party software, including Adobe, Java, Firefox, Chrome, and Windows. It seamlessly operates on both computers and servers, designed to support remote workforces.
3. Block Common Entry Points from Email
Implement robust email filtering systems to intercept malicious attachments and links before they reach your employees’ inboxes. ArmourZero’s Email Security service is powered by Avanan, capable of blocking spam and malicious emails to thwart phishing attempts.
4. Antivirus Protection
Safeguard your systems with antivirus software installed on all hosts, ensuring real-time detection and regular updates. ArmourZero offers EDR (Endpoint Detection and Response), EDR with WI (Web Isolation), AV (Antivirus), and NGAV (Next-Generation Antivirus) as a service powered by Crowdstrike and WithSecure.
5. Web Security
Employ DNS filtering, which uses the Domain Name System to block malicious websites and filter out harmful or inappropriate content. This ensures data security and enables organisations to control employee access on company-managed networks. ArmourZero provides a web protection service powered by DNSFilter.
6. Prevent Malicious Encryption
Deploy Endpoint Detection and Response (EDR) software like EDR with Threat Intelligence as a service powered by Crowdstrike. This uses various detection techniques to identify ransomware and offers ransomware rollback to restore damaged system files.
7. Scan your security posture to understand your cyber risk
Security rating as a service gives you accurate, non-invasive visibility into your vendors’ security postures and then ranks vulnerabilities in order of priority, so you know which issues to tackle first.By understanding the Security Rating—and inherent cyber risk—of third-parties, security teams get a simple snapshot of an organisation’s security posture.
Monitoring and Detection Services
Monitoring and Detection are essential components of a robust cybersecurity strategy:
1. Advanced Threat Detection
It involves having a well-equipped Security Operations Centre (SOC) that possesses advanced capabilities in identifying and responding to emerging threats. This includes proactive threat discovery, precise threat detection, comprehensive investigation, and swift incident management. The ArmourZero SOC team ensures it remains updated with the latest threat intelligence through ongoing professional training, guaranteeing a proactive stance against evolving cyber threats.
2. Cybersecurity Awareness Training
To bolster your organisation’s defences, it’s crucial to invest in cybersecurity awareness training for your staff. This training educates employees about cybersecurity best practices, potential threats, and how to recognise and respond to security risks. By increasing employee awareness, you create an additional layer of defence against social engineering and other cyberattacks.
3. Password Policies
Robust password policies are fundamental for safeguarding sensitive data. Adhering to stringent password standards, such as the use of complex, regularly updated passwords and multifactor authentication, enhances security. Implementing strong password policies helps prevent unauthorised access and minimises the risk of data breaches.
4. Account Monitoring
Keeping a vigilant eye on servers, end-users, and Active Directory is critical to promptly detect any unrecognised or suspicious devices attempting to access your network. ArmourZero offers a consolidated Devices page, which simplifies the process of monitoring and managing account activities, ensuring that unauthorised access attempts are promptly identified and mitigated. This proactive approach enhances your organisation’s overall security posture and reduces the risk of security breaches.
ArmourZero provides a wide range of services designed to cater to various endpoint types, allowing you to comprehensively orchestrate your endpoint security.
Protecting your endpoints is paramount in today’s threat landscape, and ArmourZero is here to provide tailored solutions to keep your systems secure. Ready to get started? Try ArmourZero services now and book your demo. A list of ArmourZero services can be found here.

Written by:
Nadia Ishak (Customer Success), Seasoned B2B Customer Success Expert for SMEs, Mid-Enterprise, and Large Corporations.
Share this post
Related Posts

5 Ways ArmourZero DevSecOps Simplifies Security for DevOps
- 02 May 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Discover how ArmourZero ScoutTwo, the AI-powered unified DevSecOps platform, simplifies security for DevOps. Let ScoutTwo empower your development life cycle.

Earth Day: The Connection of Cybersecurity and Sustainability
- 22 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Uncover the link between Earth Day and Cybersecurity, promoting sustainability through data protection and environmental stewardship. Let’s secure a greener future.

What is DevSecOps? Definition & Best Practices for Tech Industries
- 18 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Learn about DevSecOps, principles, and best practices for the tech industry. Integrate security seamlessly into software development and enhance quality.

Safeguarding Your Organisation During the Hari Raya Holiday
- 09 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Protect your organisation from holiday cyberattacks during Hari Raya. Learn more about the risks and best practices for holiday security with ArmourZero.

