What is Security-as-a-Service?
(SECaaS)
Definition and Benefits
Definition of Security-as-a-Service (SECaaS)
Security-as-a-Service (SECaaS) provides security services with combined technology, people and processes on one subscription basis hosted and managed by cybersecurity cloud providers such as ArmourZero. Similarly to Software-as-a-Service (SaaS), SECaaS solutions have become increasingly popular and important for many organisations as a way to ease the in-house IT team’s responsibilities, the scale security needs as the business grows, and to avoid the costly and maintenance of on-premise alternatives.
Irrespective of your industry or organisation’s size or complexity, a robust cybersecurity infrastructure is the key to protecting your asset. But common problems prevail for IT personnel monitoring or managing potential threats: a constant triage of alerts, dispersed information that are challenging to gather, and lack of time, tools, skillset or resources to effectively protect your organisation.
Nowadays, with applications in the cloud and users connecting everywhere, it is increasingly difficult to just adopt on-premises based security solutions.
Reality check:
- More SaaS applications are in use than those hosted locally, eg email
- More work is performed off the office network than on it, eg work-from-home
Benefits of SECaaS
A true SECaaS covers nothing less than some benefits below:
1. Save cost
This eliminates the huge cost of deployment of on-premise security solutions at your office or data centre such as appliance (hardware), servers for management console and its databases. That includes eliminating the on-premise services required!
Subscription tiers, the more subscriptions, the higher the tier of discount.
2. Save time
No hardware or software is needed for purchase. Security protection starts almost instantly, not in weeks.
3. Faster user provisioning
No more tedious on-premise user installation, it’s automated user provisioning.
4. Faster threat response and increased security
Round the clock security threats and alerts monitoring; 24 hours, 7 days a week, 365 days a year (24/7).
5. Expertise covered
Highly skilled security experts are costly, and you can have them without being on your payroll. The IT team can now focus on what is important for your organisation, leaving the tedious administration job to us.
6. Latest technology
No longer need to worry and deal with ever-changing or obsolete solutions. Technology is covered by the service that delivers.
7. Latest updates with no boundary
Wherever your users are, as long as they are connected to the Internet, the latest patch can be easily deployed to ensure you receive the latest updates.
8. Flexible pricing with plan options
Easy and flexible pricing; just pay what you need with monthly or yearly subscription options.
9. License Management
View and store all licenses into one console, start and expire date.
SECaaS subscribing model
You just need to pay a flat fee based on the unit price, depending on the service that you subscribed to with no other hidden services cost! For example, in Email Security Protection as-a-services, you just need to pay a flat “service fee per user“ which includes the technology’s license. You have the option of choosing based on per month or per annual subscription basis.
ArmourZero subscription is built in tiers, the more you subscribe, the more the subscription price will be reduced.
Comparison between traditional on-premise and SECaaS
Infrastructure setup
The traditional on-premise deployment is often very costly. You need to purchase servers or appliances with databases, software and licenses, and let’s not forget the facility and utility needed to ensure the on-premise infrastructure is working well.
Since on-premise deployment centralised all the security policies and patches locally, all traffic for the remote and off-network users are forced to connect back to the office or centralised data centre through a complex configuration and access controls that will result in a terrible user experience such as virtual private network (VPN).
Cloud applications were designed to be accessed directly through local internet breakouts. There is totally no hassle to go through all the above. With cloud-delivered SECaaS models, it brings security to the users.
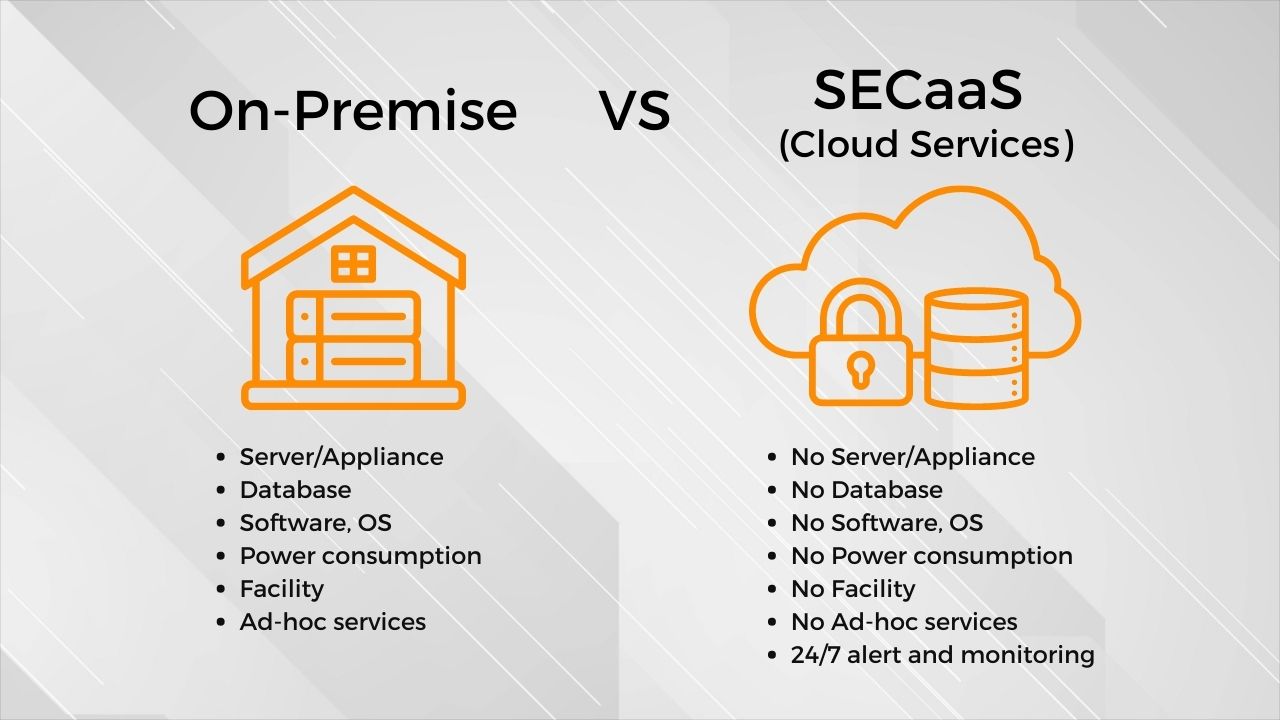
Comparison between traditional on-premise and SECaaS
Cost analysis
The cost comparison is various compared to the solution, scope and many more. Nevertheless, nothing is more simple than just subscribing to SECaaS, which is inclusive of infrastructure and all services that are needed the most.
Below is the approximate cost between traditional and SECaaS. You can see a tremendous price difference due to the evolution of technologies and services.
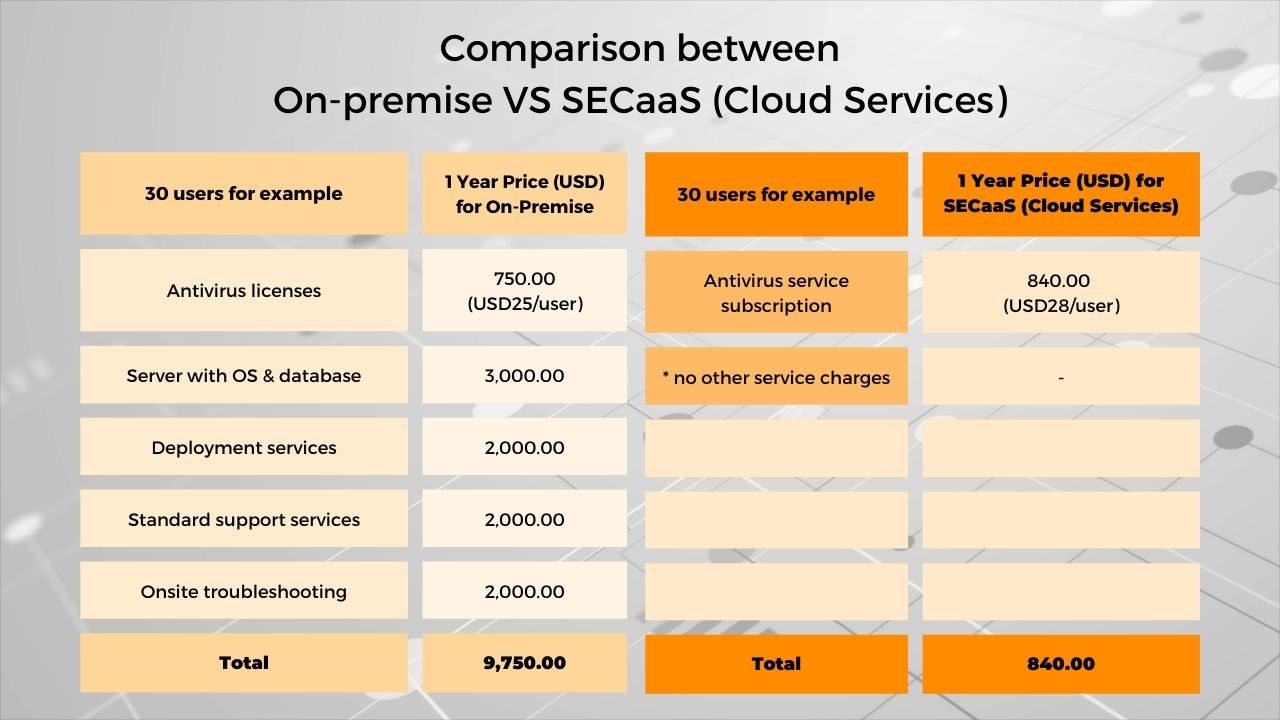
Protect your organisation from cybercrime and cyber threats today with just one click!
See our pricing comparison here, and request a demo to understand further.
You can also contact our sales to help you choose the right cybersecurity services for your business.
![]()
Written by:
Vivian Wong (VP Marketing at ArmourZero). Digital Marketing expert with vast experiences in marketing field.
Share this post
Related Posts

Earth Day: The Connection of Cybersecurity and Sustainability
- 22 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Uncover the link between Earth Day and Cybersecurity, promoting sustainability through data protection and environmental stewardship. Let’s secure a greener future.

What is DevSecOps? Definition & Best Practices for Tech Industries
- 18 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Learn about DevSecOps, principles, and best practices for the tech industry. Integrate security seamlessly into software development and enhance quality.

Safeguarding Your Organisation During the Hari Raya Holiday
- 09 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Protect your organisation from holiday cyberattacks during Hari Raya. Learn more about the risks and best practices for holiday security with ArmourZero.

Cyberattacks: A Growing Threat to Higher Education
- 02 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Universities hold sensitive data but face cyberattack risks in the digital age. Explore the impact of cyberattack and learn how to protect your institution.


