What is Social Engineering
in Cybersecurity?

Social engineering is one of the most subtle and insidious types of cyberattacks. This type of attack uses human psychology to overcome the weaknesses of technology, making it a difficult challenge for individuals and organisations. In this article, we will enter the world of social engineering attacks, life cycle, examples, and ways to protect your organisations or yourself.
What are Social Engineering Attacks?
Social engineering attacks are tactics used by cybercriminals to trick individuals or groups into revealing sensitive information. If their tactic works, the attacker will encourage the victims to give away information such as PINs, passwords, date of birth, or bank account details. Or they may encourage the person to visit a malicious website that can damage their computer.
Therefore, unlike traditional cyberattacks that target technical vulnerabilities, social engineering attacks exploit human weaknesses, psychology, emotions, and behaviours to gain unauthorised access to sensitive information or other objectives.
Social engineering is a very dangerous attack because it can be successful by fooling one victim that can provide enough information to create an attack. Nowadays, social engineering attacks in cybersecurity have become more sophisticated because the phishing emails or fake websites look realistic enough to fool the victims.
Social Engineering Life Cycle
The social engineering life cycle outlines the various stages that an attacker goes through when planning and executing a social engineering attack. It’s important to understand this life cycle to better defend against social engineering threats. In its simplest form however, the Social engineering lifecycle follows four basic phases: Investigation, Hook, Play, and Exit.
1. Investigation phase
Investigation phase in social engineering attacks involves the attacker conducting research to gather information. Target selection could be based on factors like organisational position or accessibility, or a broader range of targets might be considered. Public sources such as social media, company websites, and profiles offer a plethora of information for attackers to exploit.
2. Hook phase
Hook phase encompasses the initial interaction with the target, which can take the form of emails or in-person contact. During this phase, attackers craft deceptive narratives to manipulate victims effectively.
3. Play phase
In the Play phase, the attacker establishes a stronger presence and executes the attack. Depending on their objectives, they may either disrupt operations or pilfer sensitive and valuable data.
4. Exit phase
Exit phase marks the end of the life cycle. The social engineer endeavours to erase any trace of their involvement and conclude their deceptive activities. The insights gained and information acquired are then leveraged in subsequent attack cycles to more proficiently deceive another victim.
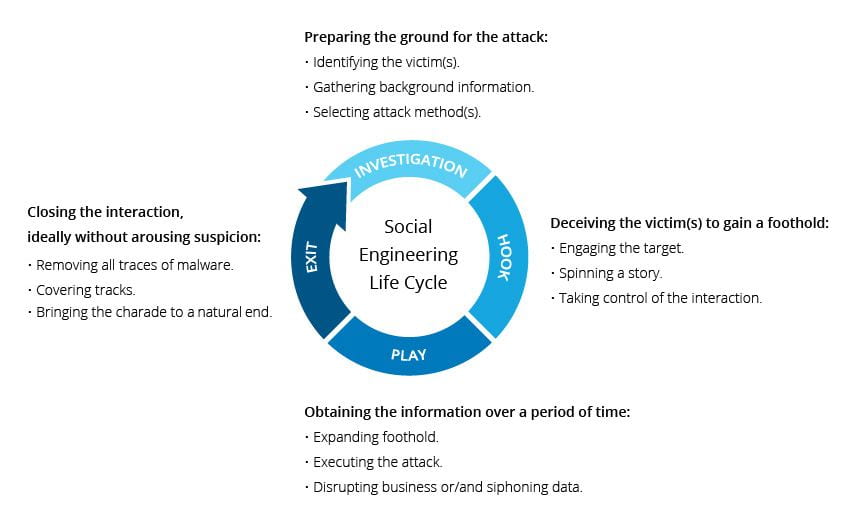
Social Engineering Life Cycle
(Source: The George Washington University Blog)
5 Types of Social Engineering Attacks

Social engineering attacks come in different ways and can occur in any social environment. The following are the five most common forms of social engineering that happened in organisations:
1. Phishing
Phishing scams are the most common form of social engineering attack. Phishing scams often take the form of emails that impersonate legitimate entities, such as banks, online services, or trusted organisations. Attackers meticulously craft these emails to appear genuine, complete with official logos and convincing language. The goal is to convince recipients to take actions that compromise their security. Phishing campaigns exploit both individual targets and organisational vulnerabilities, making them highly effective and damaging.
Phishing attack real-life example:
In 2021, a series of phishing attacks and subsequent malicious transactions impacted customers of Oversea-Chinese Banking Corporation (OCBC), resulting in approximately $8.5 million in losses for around 470 customers. The attacks involved customers falling for phishing emails and disclosing their account details, leading to a rapid escalation of fraudulent activity despite the bank’s efforts to shut down fraudulent domains and warn customers.
Once the phishing campaign gained traction, the attackers established “mule” accounts to receive stolen funds. The bank’s security team faced challenges as the fraudsters quickly replaced shut-down mule accounts with new ones. After bringing the situation under control, the CEO faced a dilemma regarding customer reimbursement – while compensating affected customers felt morally right, Wong was concerned it might encourage more attacks. As of now, over 200 customers have been reimbursed for their losses.
Read more: How to Prevent Phishing Attack
2. Business Email Compromise (BEC)
Business Email Compromise (BEC) attacks represent a sophisticated form of cyber fraud that exploits the trust and authority associated with C-level executives within organisations. In a BEC attack, the attacker strategically impersonates a high-ranking executive, typically a CEO, CFO, or other top official. These attacks aim to manipulate employees, often in financial roles or those with access to sensitive data, into carrying out actions that serve the attacker’s ulterior motives. The impersonation is usually carried out through emails, but can also extend to phone calls, creating a multi-faceted approach that increases the chances of success.
In a typical BEC attack, the attacker crafts convincing emails that resemble legitimate communication from the executive, using the executive’s name, email address, and even their writing style. The attacker may initiate requests that seem like routine business activities, such as authorising a financial transaction, approving a payment, or sharing sensitive data. The recipient, believing the message to be genuine due to the perceived authority of the sender, unknowingly complies with the request, often resulting in substantial financial losses or data breaches.
BEC real-life example:
Microsoft 365 phishing scam steals user credentials, in April 2021, a noteworthy Business Email Compromise (BEC) scheme was uncovered, introducing a deceptive tactic involving the installation of malicious code onto the recipient’s device. The attack commences with an innocuous-looking email bearing a subject related to a “price revision,” accompanied by an attachment that resembles an Excel spreadsheet (.xlsx) but is, in reality, a .html file in disguise.
Upon opening the seemingly benign .html file, the recipient is redirected to a malicious website hosting code designed to trigger a pop-up notification. This notification falsely asserts the user’s logout from Microsoft 365, urging them to re-enter their login credentials. Unsurprisingly, this action plays right into the hands of the cybercriminals orchestrating the scam, as the credentials are promptly transmitted to them via a fraudulent web form.
3. Watering hole attacks
Watering hole attacks represent a sophisticated and targeted form of social engineering, aiming to ensnare specific groups of individuals by compromising websites that these groups are likely to visit. Unlike more direct attacks, where cybercriminals target individuals or organisations directly, watering hole attacks involve a more subtle approach that leverages the trust associated with legitimate websites.
In a watering hole attack, attackers identify websites that are frequently visited by their intended targets. These websites are often associated with the targets’ interests or professions, making them more likely to be accessed. Once a suitable website is identified, attackers compromise it, typically by injecting malicious code or malware into the site’s content or infrastructure. When a member of the target group visits the compromised website, their device becomes vulnerable to infection.
Watering hole attack real-life example:
The 2013 Target data breach serves as a notable illustration of a successful watering hole attack with far-reaching ramifications. The breach originated from hackers exploiting a vulnerability in Target’s point-of-sale (POS) systems, granting them entry to pilfer data from over 40 million credit and debit cards used by Target patrons. Subsequent investigation revealed that the attackers had initiated their breach by infecting a third-party vendor’s website with malware. This vendor offered heating and ventilation services to Target stores, thus providing the attackers a gateway into Target’s networks.
The aftermath of the Target data breach reverberated throughout the business landscape, underscoring the necessity of robust cybersecurity protocols and meticulous scrutiny of third-party vendors. The breach led to substantial consequences for Target, including plummeting stock prices, eroded customer trust, and agreed to pay $18.5 million to settle claims by 47 states. After the incident, Target committed over $250 million to enhance cybersecurity and introduced an employee education initiative on cybersecurity matters.
4. Physical social engineering
While digital threats often take centre stage, the significance of countering physical vulnerabilities cannot be overlooked. Specific individuals within an organisation, including help desk personnel, receptionists, and frequent travellers, face elevated susceptibility to in-person physical social engineering attacks, which exploit human interactions and manipulation.
Shielding against physical social engineering necessitates a comprehensive approach encompassing various security controls. Establishing strong physical security measures, such as maintaining visitor logs, enforcing escort requirements for authorised personnel, and conducting thorough background checks, plays a pivotal role in thwarting potential threats. These measures create layers of defence against unauthorised access and manipulation by external individuals with malicious intentions.
Physical social engineering real-life example:
In 2015, “fake CEO” scam that targeted Mattel, a multinational toy company. In this physical social engineering attack, the scammer posed as the CEO of Mattel and engaged in fake communications with the company’s finance department. The scammer convinced the finance team to transfer $3 million to a bank account in China, under the pretence of an acquisition deal. The scam was detected only after the funds were transferred, leading to a substantial financial loss for the company. This real-life example underscores the need for not only digital cybersecurity, but also comprehensive physical security measures to counteract sophisticated forms of manipulation and deception that can occur in person.
5. USB baiting
The USB baiting technique involves cybercriminals preloading malware onto USB drives, then discreetly leaving these compromised devices in targeted locations. USB baiting is also called USB attack. The objective is to entice unsuspecting individuals into picking up the USB drives and plugging them into their organisation’s systems, inadvertently initiating a chain reaction of malicious code dissemination within the corporate environment.
The essence of USB baiting lies in its deceptive simplicity. The strategy capitalises on the human tendency to be curious or opportunistic, as individuals who find abandoned USB drives might be inclined to connect them to their computers out of curiosity or in the hope of discovering valuable data. However, the consequences are far from benign, as the inserted USB drive can deliver malware capable of infiltrating the network, extracting sensitive information, or facilitating a full-scale cyberattack.
USB baiting real-life examples:
The Stuxnet attack was a groundbreaking example of a highly sophisticated and targeted cyberattack that exploited USB drives. Unleashed around 2010, Stuxnet was a complex worm specifically designed to compromise industrial control systems, particularly Iran’s nuclear program. The attack involved infecting USB drives with the Stuxnet malware, which then spread to air-gapped systems by leveraging USB connections. This allowed the malware to stealthily infiltrate and disrupt Iran’s uranium enrichment centrifuges by manipulating their programmable logic controllers (PLCs), causing significant damage to the nation’s nuclear infrastructure. Stuxnet underscored the potential of USB-based attacks to breach even isolated systems, highlighting the need for stringent cybersecurity measures and defence strategies.
Read more: Types of Social Engineering Attacks
How to Protect Your Business against Social Engineering Attacks?

Your organisation can take several measures to defend against social engineering attacks:
-
Employee Training
Regularly educate employees about the different types of social engineering attacks, how to recognise them, and what actions to take to prevent falling victim. Implementing consistent and tailored training for your organisation is a crucial strategy in fortifying your defence against social engineering attacks. This training should encompass hands-on demonstrations that vividly illustrate the various tactics attackers might employ to manipulate your employees.
-
Security Policies
Organisations should establish clear and comprehensive security policies to guide employees in making sound decisions when confronted with social engineering attempts. Create security policies that outline procedures for verifying identities, handling sensitive information, and reporting suspicious activities.
-
Password Management
Enforcing guidelines such as complexity requirements, regular password changes, and the mandate to never share passwords, irrespective of the requester’s position, bolsters the security of valuable information assets. Also, add an extra layer of protection against unauthorised access.
-
Multi-Factor Authentication (MFA)
For heightened security, high-risk network services like modem pools and VPNs should implement multi-factor authentication, elevating protection beyond static passwords.
-
Email Protection and Anti-Phishing Attacks
Employing layered email protection can mitigate the risk of phishing and other social engineering attacks. Some email security tools come equipped with built-in anti-phishing measures, adding an extra layer of defence against deceptive emails.
Read more: How to Defend Against Social Engineering Attacks?
Protect your organisation from social engineering attacks today with just one click!
See our pricing here and request a demo to understand further.
You can also contact our sales to help you choose the right cybersecurity services for your business.
![]()
Written by:
Fanny Fajarianti (Performance Marketing). Experienced digital marketer in the information technology and services industry.
Share this post
Related Posts

Earth Day: The Connection of Cybersecurity and Sustainability
- 22 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Uncover the link between Earth Day and Cybersecurity, promoting sustainability through data protection and environmental stewardship. Let’s secure a greener future.

What is DevSecOps? Definition & Best Practices for Tech Industries
- 18 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Learn about DevSecOps, principles, and best practices for the tech industry. Integrate security seamlessly into software development and enhance quality.

Safeguarding Your Organisation During the Hari Raya Holiday
- 09 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Protect your organisation from holiday cyberattacks during Hari Raya. Learn more about the risks and best practices for holiday security with ArmourZero.

Cyberattacks: A Growing Threat to Higher Education
- 02 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Universities hold sensitive data but face cyberattack risks in the digital age. Explore the impact of cyberattack and learn how to protect your institution.

