World Password Day:
Armour Your Password
to Avoid Attacks
Intel created World Password Day and commemorated the first Thursday of May (This year, 2022, is on May 5th) to address the urgent need for strong passwords. Most operating systems provide an easy way to create and store passwords.
World Password Day brings awareness of the importance of strong passwords and why everyone needs to change their passwords every few weeks. The leakage of passwords can compromise your digital ID and personal information. Unfortunately, not many people are accustomed to changing passwords frequently, even though they know the risks.
Take World Password Day as an opportunity to change your email, social media account, and most importantly, the password of the account that stores your personal information immediately.
We will invite you to take serious action to Armour your password through this blog. Topics that we will discuss are:
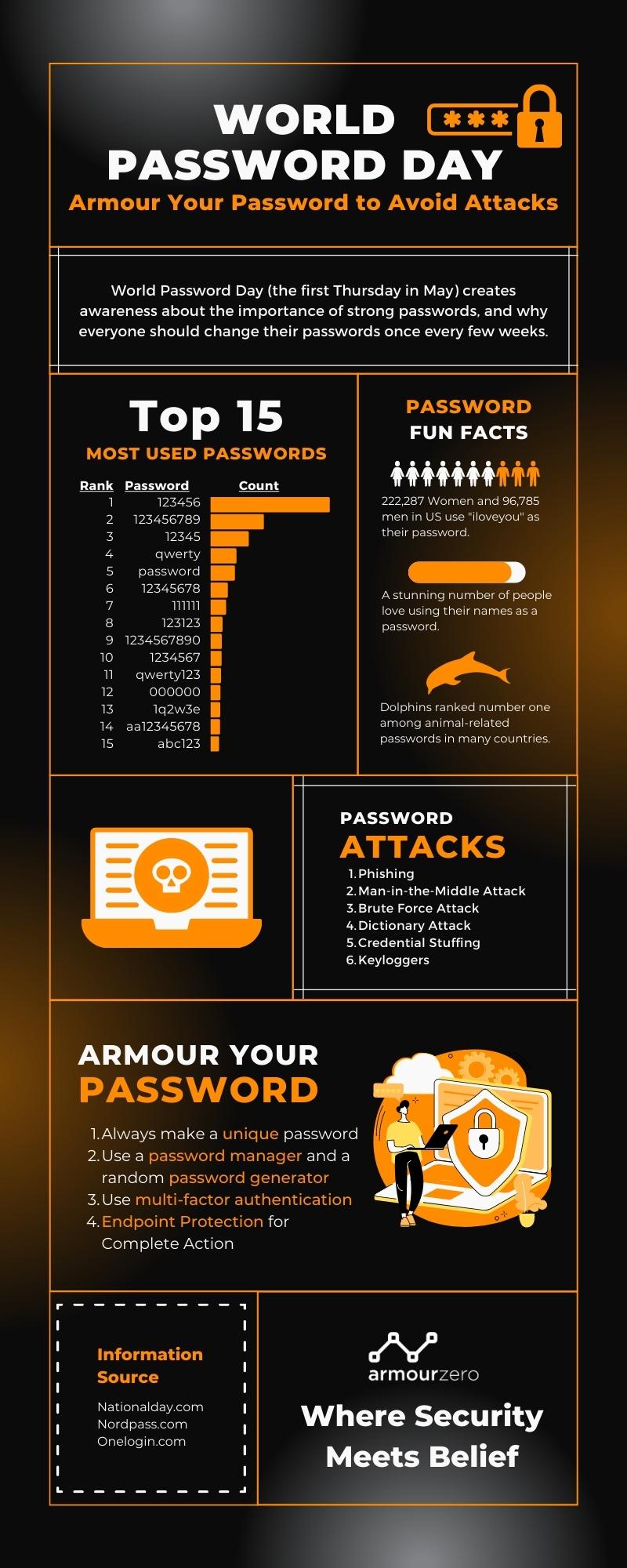
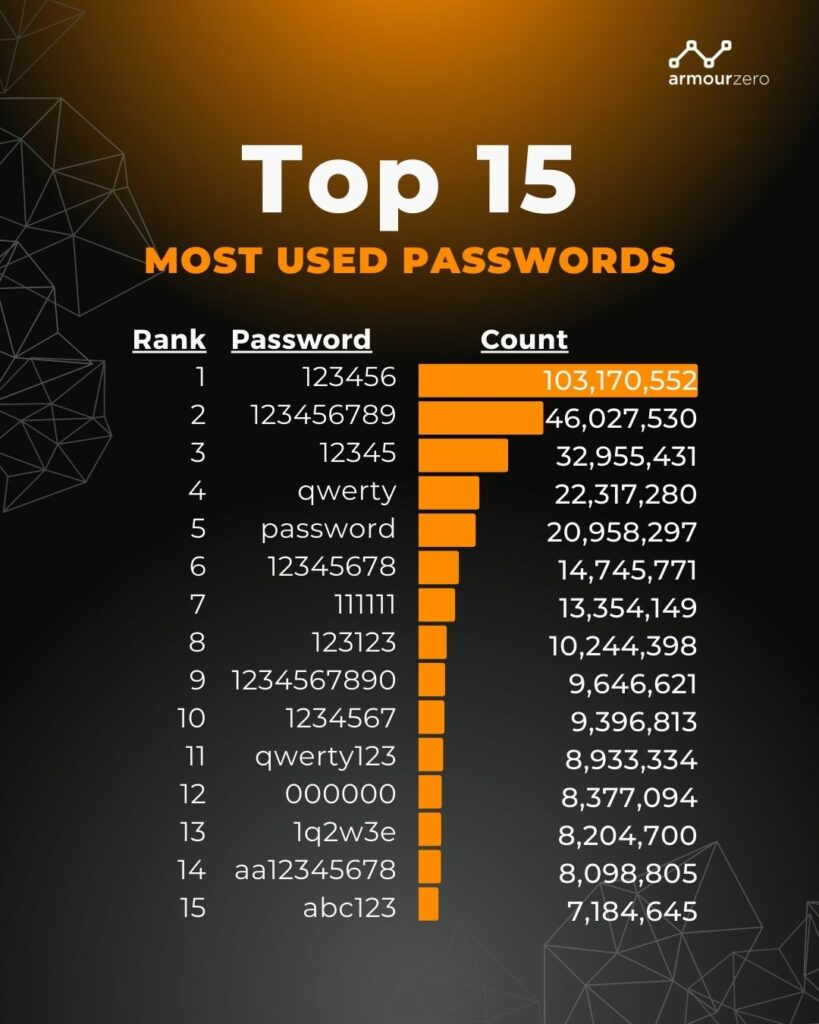
Top 15 Most Used Passwords
It’s understandable to choose a password that is easy to remember. The average person has over 100 different online accounts that require a password. However, simple passwords are so easy for hackers to understand that they can easily access their personal information and accounts.
Lookout said in a December post that an average of 80% of consumers leaked emails to the dark web. You can easily belong to that majority without knowing it. According to Lookout, these leaked emails often lead hackers directly to theft of passwords and personal information in other online accounts. Below is a list of the 15 most used passwords from Nordpass:
Password Fun Facts
Aside from the Top 15 Most Used Passwords, there are some fun facts about passwords that most people use because it is also easy to remember.
-
- More women (222,287) in the US, use “iloveyou” for their password than men (96,785).
- A stunning number of people love using their names as a password.
- Ferrari and Porsche are the most popular car brands for bad passwords.
- Swear words are quite often used as passwords. Research shows that men use swear words as passwords more often than their female counterparts.
- One direction makes a comeback to the list of the most common passwords in several countries after mysteriously vanishing from the 2020 list.
- Liverpool might be the most popular team globally, judging by how many times it has been used as a password.
- This year, dolphins ranked number one among animal-related passwords in many countries.
Password Attacks
Password attacks are one of the most common forms of corporate and personal data breaches. Password attacks are easy when hackers try to steal passwords. In 2020, 81% of data breaches were due to credential breaches. Passwords are less secure because they can contain only a limited number of letters and numbers. Hackers know that many passwords are not properly designed, so password attacks remain an attack vector.
According to Onelogin, six types of password attacks might hit us anytime. You should beware of these attacks:
1. Phishing
Phishing is when a hacker disguised as a trusted party sends a fraudulent email hoping that you will voluntarily provide personal information. They lead you to a fake “password reset” screen from time to time. Otherwise, the link will install malicious code on your device.
Related Article: Phishing: Definition, Types of Attacks, and Examples
2. Man-in-the-Middle Attack
Man-in-the-middle (MitM) is an attack when a hacker or compromised system sits between two non-breached people or systems and decrypts information passed to each other, such as passwords. If Alice and Bob pass notes in class, but Jeremy needs to pass those notes, Jeremy has the opportunity to be an intermediary. Similarly, Equifax removed the app from the App Store and Google Play Store in 2017 because it shared sensitive data through insecure channels hackers may have used to steal customer data.
3. Brute Force Attack
A brute force attack uses a battering ram if the password is equivalent to using a key to open the door. Hackers can try 2.18 trillion password and username combinations in 22 seconds. If the password is simple, your account may be cross-shaped.
4. Dictionary Attack
A type of brute force attack, a dictionary attack, relies on our practice of choosing “simple” words as passwords. The most common is what hackers put together in a “crack dictionary”. More advanced dictionary attacks include personally essential words such as place of birth, child’s name, pet’s name, etc.
5. Credential Stuffing
If you’ve been hacked in the past, you know that your old password may be posted on a dubious website. Credential stuffing uses an account whose password has never been changed after an account violation. Hackers try different combinations of old usernames and passwords, hoping that the victim will not change them.
6. Keyloggers
The keylogger is malicious software designed to track every keystroke and report it to hackers. Users usually download software believing that installing a keylogger without notice is justified.
Armour Your Password
To prevent yourself from those password attacks, you may need a strong password. Remember to protect yourself and your information, you need to use long, strong, and complex passwords for others to guess, but you are still relatively easy to remember. We have summarised some tips that may help you armour your password and data.
1. Always make a unique password
Stay away from the obvious, which means, never use consecutive numbers or letters. Don’t use the Top 15 Most Used Passwords as your password if it’s related to internet data. Consider a unique password that does not contain personal information such as your name or date of birth. Hackers use everything they know about you to guess, especially if you’re the target of password hacking.
- Make it long, this is the most critical factor of a strong password. It would be better to use not less than 15 characters. The more characters you use, the stronger your password is.
- Use a mix of characters (upper-case and lower-case), numbers, and symbols. Use as much as possible, to have a unique password. This will prevent you from getting a brute force attack to crack your password.
- Don’t use memorable keyboard paths. Much like the above advice, do not use sequential letters and numbers, and do not use sequential keyboard paths (like qwerty). These are among the first to be guessed.

2. Use a password manager and a random password generator
Password Manager keeps track of all passwords and does everything except one, the Master Password, which allows access to Password Manager. This will help you to collect every password you have, so you don’t need to remember everything. Keeping your passwords on the password manager is not the same as writing down your passwords or sharing the password with your friends. You can take a look at some password manager recommendations here.
Apart from that, you can also use a password generator to help you create strong passwords. There are several password generators that you can find online, one of which is this. The password manager uses a pseudo-random algorithm. This algorithm starts with a number called a seed, then they’ll get a new number with no traceable connection to the old number, and the new number becomes the next seed. The original seed will not be displayed again until every other number is displayed.
3. Use multi-factor authentication
Multi-factor Authentication (MFA) adds a layer of protection (this will be the first layer of protection if your account details are compromised). These have become new industry standards for adequate security. Avast also explains, on their blog, how to use them and how to add MFA to popular social accounts such as Twitter and Facebook. In addition to the password, you will need something like Biometrics data (fingerprint, eye scan, etc.) or a physical token. That way, no matter how simple or complex, passwords are only half the puzzle.
4. Endpoint Protection for Complete Action
As a company or organisation, it will be too hard to control the employees’ passwords, especially if you’re implementing remote working. The IT person can’t track the password, and it will be hard to know where the data leak comes from. Then, maybe you require an Endpoint Protection and Patch Management to help protect your whole organisation and company.
Endpoint Protection service could help you protect your endpoints and assets against known cyber threats and breaches from commodity malware to sophisticated attacks, including ransomware with antivirus and more. Patch Management service will help you protect all your Operating Systems and third-party applications, such as Microsoft Office, Adobe etc., against known vulnerabilities. Patch Management will control authorised/unauthorised applications used, ensuring continuous patches and up-to-date versions are released by the application vendor.
Also, get our 1-year free limited promotion for Endpoint Protection with EDR as-a-service here.
![]()
Written by:
Bernadetta Septarini (Content Marketing). Experienced content marketing and social media in the information technology and services industry.
Share this post
Related Posts

Safeguarding Your Organisation During the Hari Raya Holiday
- 09 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Protect your organisation from holiday cyberattacks during Hari Raya. Learn more about the risks and best practices for holiday security with ArmourZero.

Cyberattacks: A Growing Threat to Higher Education
- 02 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Universities hold sensitive data but face cyberattack risks in the digital age. Explore the impact of cyberattack and learn how to protect your institution.

Innovative Strategies for Cybersecurity in the AI Era
- 27 Mar 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Discover how AI is reshaping cybersecurity and safeguard your organisation in our latest blog post. Learn how to protect your business in today’s digital world.

Level Up Cybersecurity: How SIEM & SOAR Work Together
- 20 Mar 2024
- By:Armour Zero
- Category: ArmourHacks
Explore how ArmourZero’s cybersecurity platform unifies SIEM & SOAR for fast threat response without implementation costs or tech lock-in in this article.

