What is an
Advanced Persistent Threat (APT)?

Today’s new age business foundation is based on digital technology. The Net is another world aside from the reality which we live in. Without the virtual world digital platform, we will be living as the same pillar with civilisation which the space aliens would consider as primitive and don’t bother to have a peek; if they don’t decide to harvest us for a midnight snack.
With the rage of the Information Technology age, the value of an individual is more valuable than gold. The information of a company may make someone a millionaire.
With this, cybercrime has increasingly become more complicated and elusive, hard to detect, handled by a group of elite hackers which possess sophisticated skill sets that could pull a giant company to its knees. This could be a government, corporate sectors, research organisation, military agencies, or even the competitor of a cybercriminal organisation themselves. Wherever valuable data is stored, which could be monetised or trade for a high bargain, these groups will make their journey to fulfil their objective which could be use as:
- Investigation
- Infiltration
- Possess valuable data
- Ransom
- initiate heavy disruption to IT infrastructure
Their attack will be detailed, sophisticated and long. This long period of attack is what is called Advanced Persistent Threat (APT).
It has been reported that APTs on European institutions will increase by 30% in 2021. The Solar wind findings last year December became one of the most taunting incidents of APT attack. The actor spent a long time of six months inside OrionIT’s network to recon, infiltrate and perfected their strategy and slowly bugged their carefully crafted software undetected in the victim’s IT infrastructure. Eventually, they succeeded in their effort, exclusively exporting valuable data to be used for who knows what or how before it was discovered. But one thing is for sure, it is worth it.
An APT is a well-planned attack on any organisation. A group of hackers will investigate an entry point to land a foothold inside the victim’s network. What this means is successfully installing malware inside the targeted network. It is a long mission to obtain a success goal primarily on data theft. But it has been incidents that show other objectives such as:
- Ransomware
- Espionage
- System damage
- Crypto mining
APTs attack has been identified to undergo a certain lifecycle.
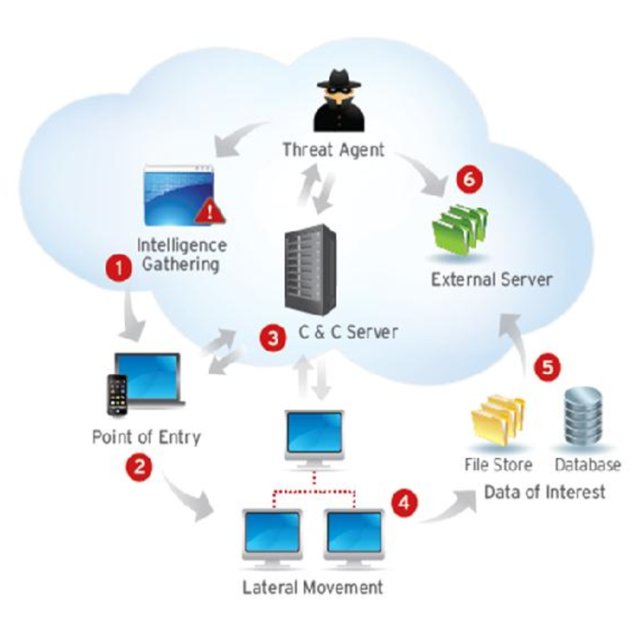
Source: Research Gate
Spear-phishing techniques are a common way of entry for a foothold. Tricking users to click a certain link, where then the link will initiate a download of malicious software in the background. This malware will then establish a communication with the actor’s command and control server, where they can use the victim’s machine to penetrate deeper into the organisation’s IT infrastructure.
The general stages of attack can be described as below.
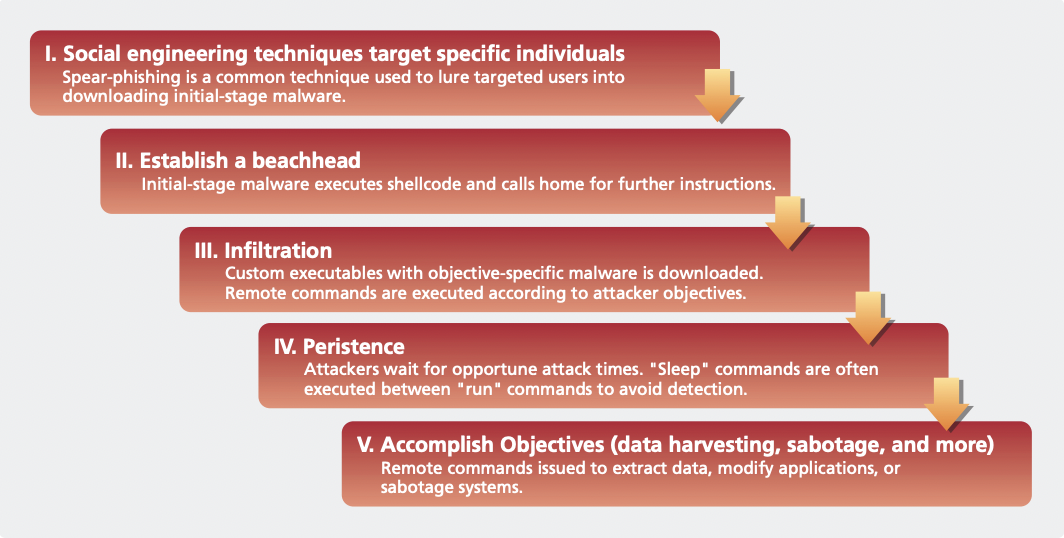
Typical APT attack steps (Source: Write Angle)
Defending from Advance Persistent Threat (APT)
Creating a defence mechanism from APT comes in the form of practice. The organisation security personnel must be trained with the right skillset to identify signs which could be the sub activities of an APT. Some activities which may be worth to look for:
- Increase late-night logging
- Trojan detection
- Unexpected data bundles
- Unexpected data flows
McAfee Advanced Threat Research (ATR) team has provided a deep insight about Operation Harvest Campaign carried out by a group of Chinese hackers and how McAfee was able to provide a solution to break the APT’s cycle for this group attack.
This is just one example which could be used as a reference to architect a solution in preventing a successful APT in a certain organisation.
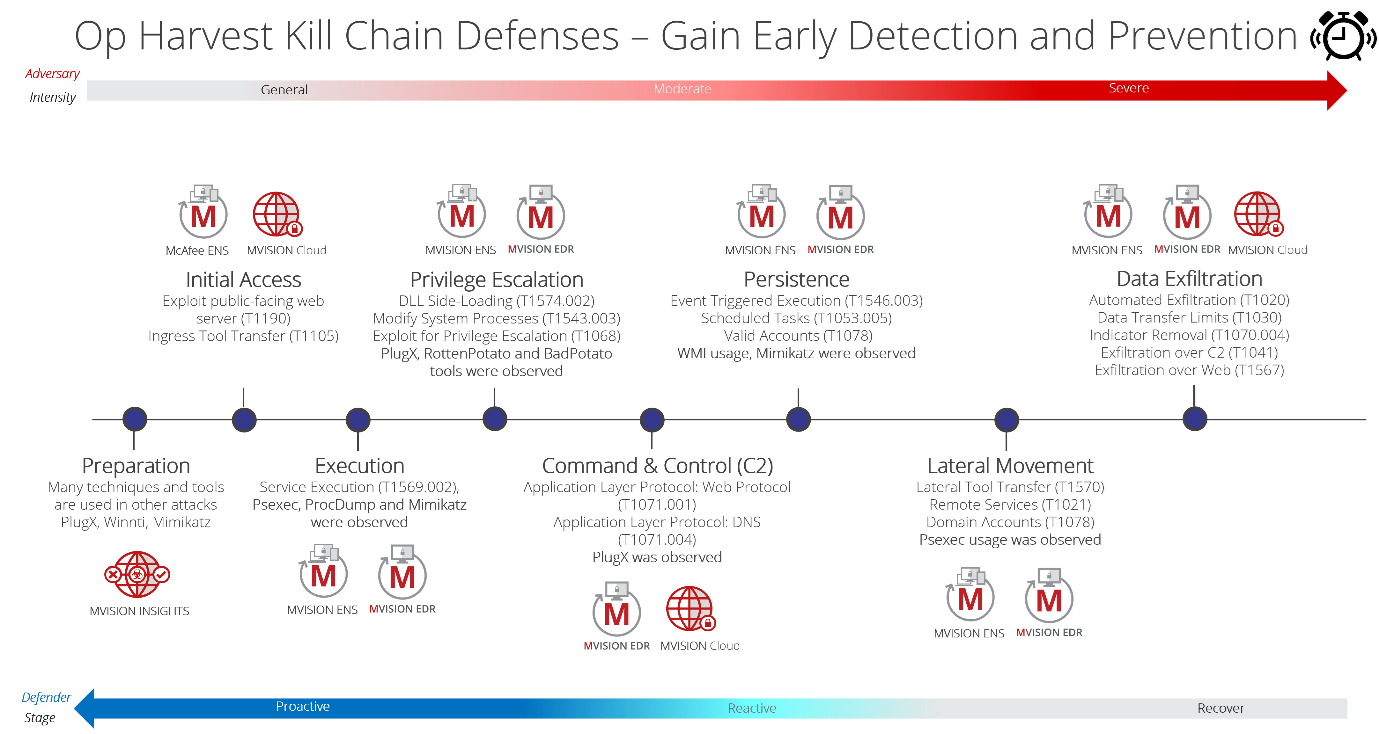
McAfee ATR team strategy to defend from Operation Harvest APT campaign.
(Source: Unifiedguru)
Final Thoughts
Advanced persistent threats are complicated, calculated, long-game attacks that can have devastating effects on an enterprise business and, unfortunately, cannot be easily predicted. However, enterprise organisations don’t have to be at the mercy of APTs. You can implement strategies that include:
- Continuous automated patching
- Advanced endpoint detection and response monitoring systems
- Multi-factor authentication and strong password protection mechanisms
- Response planning to create a big picture of what to do if a breach occurs
Deploying AI and ML based security solutions can be highly effective in detecting anomalous behaviour, which is one of the hallmarks of an APT attack.

Written by:
Mohammad Rizal Lokman, experienced IT Security in the information technology and services industry.
Share this post
Related Posts

Earth Day: The Connection of Cybersecurity and Sustainability
- 22 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Uncover the link between Earth Day and Cybersecurity, promoting sustainability through data protection and environmental stewardship. Let’s secure a greener future.

What is DevSecOps? Definition & Best Practices for Tech Industries
- 18 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Learn about DevSecOps, principles, and best practices for the tech industry. Integrate security seamlessly into software development and enhance quality.

Safeguarding Your Organisation During the Hari Raya Holiday
- 09 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Protect your organisation from holiday cyberattacks during Hari Raya. Learn more about the risks and best practices for holiday security with ArmourZero.

Cyberattacks: A Growing Threat to Higher Education
- 02 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Universities hold sensitive data but face cyberattack risks in the digital age. Explore the impact of cyberattack and learn how to protect your institution.

