End User Management:
Fundamental That Usually
Overlooked
- Published: 17 Jan 2022
- By: Ts. Saiful Bakhtiar Osman
- Category: When Experts Meet Experts (WEME)

“End User Management” is a topic that is very close to my heart. From my 22 years of journey in IT, I have seen how the end users had influenced the ups and downs of the organisation. The success and the failure of an IT initiative were also contributed by the full support or the resistance from the internal stakeholder, namely the end users.
Not to forget all the virus and malware incidents that had kept the IT awake at night. This includes familiarisation issues which contributed to the highest number of IT Call Centre’s tickets, and the End User Support Team who were cracking their heads to attend the same issues, all the time. Sounds familiar? If it does, then you must have gone through all the same pain as I did, or worse.
Why is end user management essential?
I have briefly touched on the importance of having the right pool of end users to support and run all your initiatives, in my previous article. This is because they are the ones executing all the plans, facing the customers, the doers, and the immediate end users of your system.
It is more critical from the IT Security perspective, with the arising threats and evolving method of attacks from the cyber world. We have seen how even big companies fell victim to cyber-attacks just simply because one of its users clicked open a compromised email attachment or clicked on a malicious pop-up box while browsing the internet. The impact was real, and the loss was significant.
Based on the “VARONIS 134 Cybersecurity Statistics and Trends for 2021”, it was indicated that 17% of the sensitive files in a typical organisation is accessible by all the employees, and on average, the employees have access to 11 million files. This has clearly shown us how common the organisation’s data is handled by the end users every single day.
To make matters more serious, the same report indicated that 60% of these companies have more than 500 accounts with non-expiring passwords! You can just imagine the severity should one of these accounts be compromised or fall into the wrong hands. It was also indicated that 77% of the companies in this report do not even have an incident response plan.
What are the risks?
I believe that all organisations are aware of the importance of the end users. However, most of them chose to ignore this factor for some reason or another. Maybe they are under the impression that such exposure will never impact their organisation, or the likelihood of happening is so low for them to even be concerned.
For the benefit of this article, I will narrow down only to the risk and the impact on the organisation’s data. As you are all aware, that data is the next oil. Data is everything to the organisation, be it market leads, financial, marketing campaigns or business value chains.
1. Internal Risk
Internal risk involves the end user as a person and how the behaviour may have an adverse impact on the organisation. If the organisation is still sceptical about such exposure, then the following statistics should become an eye-opener:
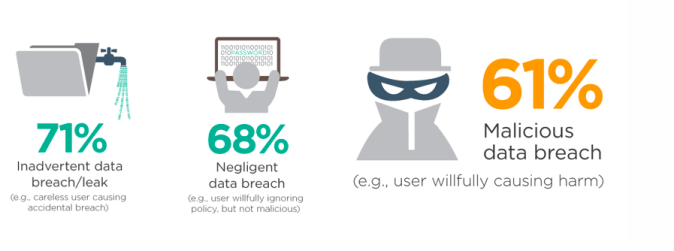
Source: readteamsecure.com
As you can see, the statistic had shown that 71% of the cases were in the “Inadvertent data breach/leak” category, in which the end users were careless or did not even realise that they had caused the data breach incident. The statistic further showed us that 68% of them were aware, but wilfully ignored the policy which subsequently led to the data breaches. What we should be concerned about is the internal perpetrators or the unlawful conduct of our employees leaking the organisation’s data for personal gain. Don’t you think that 61% is a very worrying percentage? There are indeed very high chances of happening and the impact shall jeopardise the whole business.
Apart from the above, there are also many other internal risks related to the end users as listed below, if not addressed, will affect the organisation:
- Resistance to technology change.
- Unskilled and lack of training.
- Generation gap and culture.
- Unfiltered social media exposure.
- No sense of responsibility and ethics.
2. External Risk
Dealing with the end user as a person itself is already a handful, but be wary that the external risks are no less damaging. I view that the external risks would have a bigger impact because it is a force that we could not control. As opposed to the internal risk that we can address and contain within the organisation itself. The external risks may come in the form of cyber-attacks, manipulation, scams, or industrial espionage.
If we take the cyber-attacks for example, the number of attacks reported keeps increasing year after year and the organisation is constantly at risk almost all the time. Furthermore, we could also see that of late, hackers and cyber-criminals have become more advanced and creative in finding ways to penetrate the organisations. It is an ongoing challenge for IT Heads and CIOs like us to keep up with this evolving threat landscape.
While companies spent thousands in providing the right tools and IT Security infrastructure, all these efforts would be in vain should we not address the human factor in the organisation. It is just like building a strong wall around your fortress, whilst the source of vulnerability comes from within. With all the firewall, intrusion detection and preventions, the company was still hit by the ransomware attack just simply because a user failed to follow the rule of not to open any attachment from an unverified source.
What are the potential impacts?
Up till now, we have already established why end user management is essential, and what are the risks associated with it. Next, an organisation should assess the impact to the organisation, should they choose to ignore the risks. As the saying goes, “Prevention is better than cure”. I am certain that the cost of incident recovery is much greater than taking a proactive step to prevent it from happening.
Being a PRINCE2 Practitioner, we always begin our business case statement with the worst-case scenario, “What if we do nothing”. With this approach, the Management would be able to see the severity of the case being tabled for their decision-making.
Listed here are some of the potential impacts:
– Identity theft
When a credential is stolen, the organisation is left vulnerable to any kind of damage and manipulation. The impact would be worse should the stolen ID have a high privilege access right.
– Monetary theft
Be it paying to release the data from a Ransomware attack or your organisation’s money is quietly being siphoned out from the company, the monetary loss is inevitable.
– Cancellation of contracts
If your organisation is a vendor to a big company, you may face a contract cancellation should they find out that your end users were involved in any unlawful conduct.
– The lawsuit (against you or your company)
This would add salt to the wounds, should you need to face a lawsuit originating from an incident. The demand may either come from your contractors or your customers.
– Liabilities for fines and penalties
You may also be fined or penalised by the Regulators should such a data breach or violation be happening in your organisation.
– Reputation loss
All the effort and years of hard work of building your organisation to where it is, will go to waste if any of the incidents cause your organisation to lose its reputation. You may not be able to recover from this at all.
Addressing and managing the end users
Based on the above, is there anything that we can do to prevent it? Or at least, can we mitigate the risk to a tolerable level, to reduce the adverse impact? We shall discuss further on this, in Part 2 of the “End User Management”. See you in the next article.
Catch When Expert Meets Expert by Ts. Saiful Bakhtiar Osman articles every bi-weekly Tuesday. Don’t forget to subscribe to stay connected. You are also encouraged to ask questions and seek advice from him.
Share this post
Related Posts

Cybersecurity: Achieving the ‘Hole-in-One’ of Digital Defence
- 07 Nov 2023
- By:Bernadetta Septarini
- Category: When Experts Meet Experts (WEME)
Discover the connection between cybersecurity and sports with Tony Smith, Regional VP at WithSecure. Let’s achieve the ‘Hole-in-One’ of Digital Defense.

Beware of Scare Software aka Scareware
- 21 Nov 2022
- By:Eugene Chung
- Category: When Experts Meet Experts (WEME)
What is Scare Software or Scareware? Learn more about this Social Engineering technique that aimed to scare the victim with ArmourZero mentor Eugene Chung.

Job Hunting Tips for IT Graduates
- 14 Nov 2022
- By:Ts. Saiful Bakhtiar Osman
- Category: When Experts Meet Experts (WEME)
The job market is tough and competitive. Learn some tips on how to do job hunting for IT graduates from ArmourZero’s mentor and expert Ts. Saiful Bakhtiar.

Tips to Successfully Sell a Credible Cybersecurity Solution
- 07 Nov 2022
- By:Eugene Chung
- Category: When Experts Meet Experts (WEME)
How do Cybersecurity sales convince prospects to trust their services and/or products? Learn more about it from ArmourZero’s mentor and expert Eugene Chung.

