Indonesia’s Antivirus Reliance:
A Cybersecurity Blindspot
In Indonesia, many individuals believe they are fully protected from cyber-attacks simply because they have installed free antivirus software. I try to prove it by looking closely at Google Trends data.
Over the past year, searches for “antivirus” have consistently outpaced searches for “cybersecurity.” On average, there are 1,650 searches per month for the term “antivirus,” while the term “cybersecurity” only receives an average of 150 searches per month.
This shows that many individuals in Indonesia may not be fully aware of the limitations of traditional antivirus software and the various forms of cyber protection available to them.
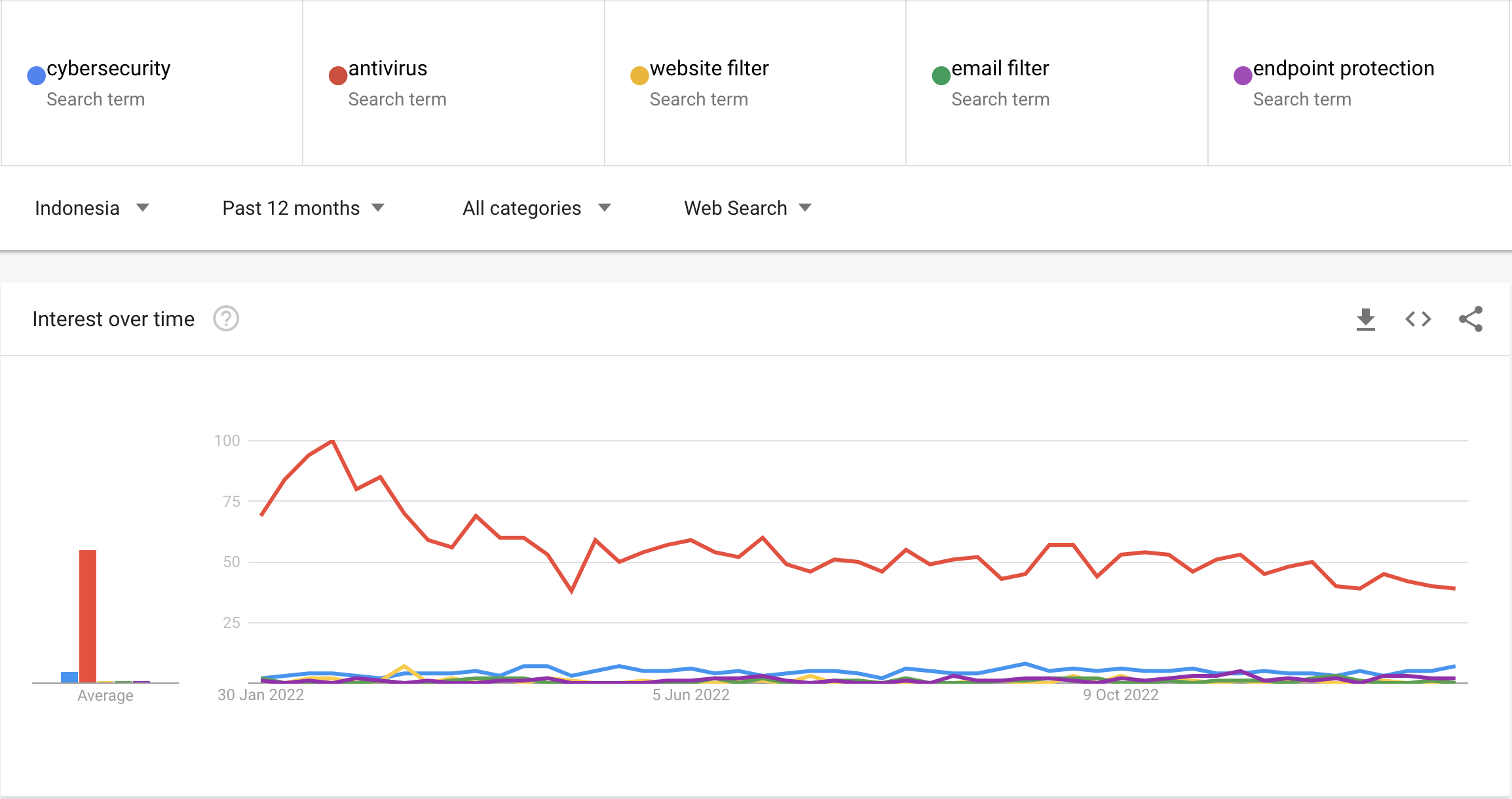
Source: Google Trends Result about Cybersecurity terms on January 30th, 2023.
Here’s the thing: relying solely on antivirus software can leave you vulnerable to other types of cyber threats. It’s a bit like trying to protect a castle with just one guard at the gate. You need a whole team of guards, each with their own specialities, to ensure the castle stays safe and secure.
This data also highlights the importance of educating and raising awareness about cybersecurity in Indonesia. Knowledge is truly power when it comes to protecting ourselves from cyber threats. And to empower you, I’ll share some valuable insights, so you won’t just rely on antivirus to protect your data.
The Potential Consequences of Antivirus Reliance
As technology continues to advance, it’s alarming to see that many in Indonesia still rely solely on antivirus software for cyber protection. This not only leaves individuals, companies, and the government vulnerable to a wide range of cyber threats, but it also puts sensitive data and valuable assets at risk. The potential consequences are numerous, and it’s crucial that immediate action is taken to address this issue and ensure proper cyber protection. Here are a few examples:
- For individuals, relying solely on antivirus software can create a false sense of security, leaving them exposed to the newest types of cyber threats. This can result in financial loss, identity theft, and damage to personal reputation.
- For companies, a lack of comprehensive cybersecurity measures can lead to data breaches, loss of sensitive information, and damage to reputation.
- For the government, insufficient cybersecurity can result in breaches of sensitive data, disruption of critical infrastructure, and damage to national security.
- Furthermore, relying on antivirus alone can lead to a lack of preparedness for cyberattacks, a lack of incident response plan and significant costs for cleanup, recovery, and restoration, as well as potential legal and regulatory fines.
Note: Antivirus software is a necessary component of a comprehensive cybersecurity strategy, but it is not sufficient on its own. A multi-layered approach to cybersecurity is necessary to protect against the full range of cyber threats.
Cyberattacks That Bypass Antivirus

Are you still under the impression that simple antivirus software can keep you safe from all cyber threats after reading the first topic? Well, let me burst that bubble for you by highlighting some types of attacks that cannot be thwarted by antivirus alone.
- Phishing attacks: These are emails or messages that appear to be from a legitimate source but are actually from an attacker. They often contain a link or attachment that, when clicked, will install malware on the victim’s computer. Antivirus software may not be able to detect this type of malware because it is new or has not yet been added to the software’s database.
- Advanced persistent threats (APTs): these are targeted attacks that are designed to gain access to a specific organisation or individual’s computer systems. They often use sophisticated techniques to evade detection by antivirus software.
- Ransomware: This type of malware encrypts the victim’s files and demands a ransom payment in order to restore access to the files. Antivirus software may not be able to detect ransomware because it does not necessarily contain a virus.
- Social Engineering attacks: these attacks use psychological manipulation to trick victims into giving away sensitive information or performing actions that will compromise their security. Social engineering attacks can bypass antivirus software because they do not rely on the installation of malware.
Cyberattacks Cases in Indonesia
If you’re still convinced that antivirus is the ultimate solution to all cyber threats, it’s time to think again. Below, I share some news about cyberattacks in Indonesia that cannot be defended solely by using antivirus software.
- Conti Ransomware attacks Bank Indonesia at the beginning of 2022. This attack resulted in a leak of Bank Indonesia data, which amounted to 74 GB. The number of Bank Indonesia’s devices that were hacked was around 237 units.
- Two thousand bank customers become victims of social engineering attacks every month. Social engineering is a cybercriminal tactic that influences the minds of customers by making emotional conditions, and this method is easier than hacking the systems.
- More than five thousand phishing attacks in Indonesia in the second quarter of 2022. The number of phishing attacks increased by around 41.52 per cent from the previous quarter. It is noted that the spread of phishing is mostly targeting financial institutions. The percentage reached 41 per cent.
The Importance of a Multi-layered Security Approach
Now that you understand that relying solely on antivirus is not enough, you may be wondering what steps to take next. Worry not, for I am here to share with you a multi-layered approach to security that will better protect you from such attacks.

- Email filters: these tools scan incoming emails for malicious content, including phishing attempts. They can block emails that contain suspicious links or attachments.
- Web filters: these tools can block access to known phishing websites and can also block malicious links in web pages, emails, and instant messaging.
- Endpoint protection: These tools, such as endpoint security software, provide real-time monitoring and protection of all devices connected to a network. This includes protection against malware, intrusion detection, and vulnerability management.
- Network security: This includes firewalls, intrusion detection and prevention systems (IDPS), and other tools that help to protect the network infrastructure. These tools can detect and block malicious traffic, such as APTs, at the network level.
- Security Information and Event Management (SIEM): These tools collect, analyse and correlate log data from various sources and provide a centralised view of the security posture of an organisation. This can help detect and respond to APTs and other advanced attacks.
- Incident response plan: This is a documented process for identifying, containing, and eradicating an APT or social engineering attack. It also includes plans for recovery and lessons learned.
- Security awareness training: this can teach employees how to recognise and avoid phishing attempts.
In conclusion, Indonesia’s reliance on antivirus software alone is a cybersecurity blindspot. While antivirus is important, it’s not enough, and you need a multi-layered security approach to fight against evolving cyber threats and reduce the risk of a successful attack. This includes technical solutions, user education, incident response planning, and an understanding of the cyber threat landscape.
*This article has been published on e27.co on Jan 30, 2023
![]()
Written by:
Bernadetta Septarini (Content Marketing). Experienced content marketing and social media in the information technology and services industry.
Share this post
Related Posts

Earth Day: The Connection of Cybersecurity and Sustainability
- 22 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Uncover the link between Earth Day and Cybersecurity, promoting sustainability through data protection and environmental stewardship. Let’s secure a greener future.

What is DevSecOps? Definition & Best Practices for Tech Industries
- 18 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Learn about DevSecOps, principles, and best practices for the tech industry. Integrate security seamlessly into software development and enhance quality.

Safeguarding Your Organisation During the Hari Raya Holiday
- 09 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Protect your organisation from holiday cyberattacks during Hari Raya. Learn more about the risks and best practices for holiday security with ArmourZero.

Cyberattacks: A Growing Threat to Higher Education
- 02 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Universities hold sensitive data but face cyberattack risks in the digital age. Explore the impact of cyberattack and learn how to protect your institution.

