End User Management:
Tackling the Issues
Right from the Root
- Published: 31 Jan 2022
- By: Ts. Saiful Bakhtiar Osman
- Category: When Experts Meet Experts (WEME)

Who is actually an End User? You may Google it and find a lot of definitions from different sources to describe this word. However, the truth is that each one of us is an End User at some point of time. You may be an IT person who is providing the services to everyone inside your organisation, but you yourself are also at the receiving end, when it comes to HR services such as payroll and medical benefits.
Now that we have established that, let us continue from where I left off in my previous article End User Management: Fundamental That Usually Overlooked. We are going to explore the possibility of nurturing a good pool of End Users and address the human factor right from the root.
Get to know your End User
When we deal with human factors, we need to accept that every single one of them is unique. They came from different backgrounds, different races or cultural beliefs and their exposures were different. I could not think of any other department than the Human Resources or Human Capital to provide the required data for us to plan and act upon.
The behaviour and the approach that we are going to take are pretty much dependent on the following:
-
Age group
Different age groups react differently to instructions and training. For diverse companies, the generation gaps usually sparked some interesting collisions between the old ways and the new ideas. No matter what the plan is, it must be something that spreads across the whole organisation so that nobody ends up being left out.
-
Gender composition
Different way of thinking, different way of working and different length of focus would be a challenge to a company. What is the gender composition like in your company? Any dominant gender group would affect how the company moves forward and adapt to changes. I am sure everyone knows how a man, or a lady carries out their work. It’s debatable though on which gender is more productive.
-
Work experience
We always welcome loyal staff who stay in a company for 20 years or possibly until retirement, because this type of staff would have a treasure of knowledge as they know every process inside and out. Nevertheless, external hiring is also good, because they bring in new ideas and experience from different companies to challenge whatever the status quo in our company. We need to handle this gently on how to show appreciation to the old staff while provoking new ideas from the external hiring staff.
-
Length of employment
Length of employment is crucial to ensure that there is continuity to all projects or initiatives. There should be consistent knowledge sharing and knowledge transfer so that the new joiners are able to continue the work, in the absence of a particular subject matter expert. We could not stop people from leaving the company, but we sure need to plan for a good succession plan and knowledge transfer to remain on track. Some companies would have been hit hard should a staff resign, and no other staff have the in-depth knowledge nor the skills to carry out what he is doing.
-
Skilled or unskilled
We must be practical when coming out with the content for IT awareness or any other initiatives. We need to cater to the right program, for the right group of people. We could not expect to give a lengthy technical jargon to a group of drivers, or non-executive group and expect them to read and comply. Not to undermine this group of people, but the approach should be something short, simple, and concise.
-
IT literacy
I believe that this part has improved over time and people are more up to date with tech devices and have very good IT literacy. However, never assume and take things for granted as there may be staff who are still very low in IT literacy, especially the older generations who are so used to doing their work manually. We need to make sure this group of people has the skills to move forward and not become the weakest link in the chain.
Assess areas to improve
Now that we know our End Users, we should next assess the areas for improvement. What is lacking and what could we do better? There are many ways for companies to carry out this type of assessment. For example, setting up a brainstorming group which consists of representatives from different age groups or departments. Yes, you may even hire an independent consultant to come onsite and conduct the assessment for you.
In my opinion, when it comes specific to IT, I would always recommend the following:
1. Invite an independent IT Security Service Provider to assess the organisation readiness
It would be best to let the independent expert do the job. They have the tools and methods to assess your overall security posture, your tech readiness, IT maturity and run the mock test or social engineering in your organisation. They would be able to share input on how other companies out there are doing to improve in this area.
2. Conduct internal assessment based on frequent IT Helpdesk cases report, random chat with users, send online Questionnaires
Don’t be surprised that your Helpdesk cases report would tell a lot about your End Users. What are the highest tickets reported? Is it password resets? User familiarisation? These figures would help you in planning which areas to improve your End Users. A simple chat with users at random also would reveal a lot of things or the struggle the End Users are facing that sometimes IT tends to ignore while implementing projects.
3. Know what is important in the organisation to be protected
I always highlight this factor during the IT events or during short interview articles that I am involved in. I find it very important for an organisation to know what information assets that are important for them to protect. Most importantly, your End Users should understand and onboard with this initiative. You would know your organisation the best because the data that is important to you may not be important to other companies. So, data classification is one way of achieving this. There is no way we could protect everything with a limited resource. That is why data classification would help you in provisioning the strictest protection to the highest confidentiality of information assets.
Devise a Training Plan
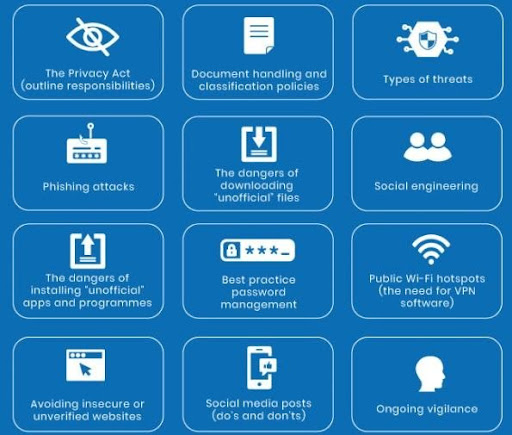
“If You Fail to Plan, You Are Planning to Fail” — Benjamin Franklin. It’s rather cliché to say this but that is the hard truth. An organisation should not be reluctant to spend time, money, and effort to devise a proper plan to improve the skills, knowledge, and awareness of their End Users. A good training plan should come with tracking to gauge the effectiveness of all the effort being implemented.
As per shown above, there are wide areas to cover, and we need to carefully plan so that all the important aspects are covered. Let’s take a phishing attack for example, nowadays, the perpetrators have become more creative in coming out with scripts to penetrate the organisations. You can refer to Eugene Chung’s article on Phishing, as he had discussed in-depth with real life examples for your reference.
Even though they are many approaches to devise a good training plan, I would suggest companies to consider the following:
-
Treat IT Security as a Training
IT Security should be treated as a normal training. Normal in the sense that it should be an ongoing effort, all year round and not something of a one-time event. IT Security should become part of the overall HR Training calendar and to involve all levels of End Users. Treating it as a training also allows a proper budget to be allocated to conduct the series of training. Unlike the old days whereby IT Training needs to be taken from IT Budget.
-
Make sure it is easy to understand
As I touched briefly earlier, it should be easy to understand so that people would acknowledge, be aware and practice in their daily work. Putting IT jargons would only make you look smart, but it would not achieve anything. So, be as layman term as possible to attract the acceptance from the crowd.
-
Monitor completion and get feedback
It would be very helpful for some companies who could afford to spend on e-Training where they could monitor the completion and progress by individual. For Financial Sectors for instance, it is important for the organisation to make sure all staff are aware and complete their Anti-Money Laundering Act (AMLA) training. E-Training would help to achieve this with reports on the overall completion as an organisation. The old fashion ways of getting feedback from users after the training would also help, for the improvement and betterment of the program.
-
Get Management support/ buy-in
It is important to get the Management’s support and buy-in for this training plan. Having the Management’s support would indicate how serious the company is in developing all their human capital. Top-down approach would also mitigate any potential resistance from any staff within the organisation.
It is no rocket science but if you approach it well, you would be able to nurture a good pool of End Users that are well informed, highly resilient, dynamic and productive in carrying out all the initiatives and directions of the company. It is like building a strong fortress, we would need the commitment from every one inside in order to defend and keep it safe.
Catch When Expert Meets Expert by Ts. Saiful Bakhtiar Osman articles every bi-weekly Tuesday. Don’t forget to subscribe to stay connected. You are also encouraged to ask questions and seek advice from him.
Share this post
Related Posts

Cybersecurity: Achieving the ‘Hole-in-One’ of Digital Defence
- 07 Nov 2023
- By:Bernadetta Septarini
- Category: When Experts Meet Experts (WEME)
Discover the connection between cybersecurity and sports with Tony Smith, Regional VP at WithSecure. Let’s achieve the ‘Hole-in-One’ of Digital Defense.

Beware of Scare Software aka Scareware
- 21 Nov 2022
- By:Eugene Chung
- Category: When Experts Meet Experts (WEME)
What is Scare Software or Scareware? Learn more about this Social Engineering technique that aimed to scare the victim with ArmourZero mentor Eugene Chung.

Job Hunting Tips for IT Graduates
- 14 Nov 2022
- By:Ts. Saiful Bakhtiar Osman
- Category: When Experts Meet Experts (WEME)
The job market is tough and competitive. Learn some tips on how to do job hunting for IT graduates from ArmourZero’s mentor and expert Ts. Saiful Bakhtiar.

Tips to Successfully Sell a Credible Cybersecurity Solution
- 07 Nov 2022
- By:Eugene Chung
- Category: When Experts Meet Experts (WEME)
How do Cybersecurity sales convince prospects to trust their services and/or products? Learn more about it from ArmourZero’s mentor and expert Eugene Chung.