How Much Does Cybersecurity Cost
and How to Budget for it?

Table of content :
- What is Cybersecurity?
- 10 Most Common Cyber Threats
- 5 Contributing Factors to Determine Cybersecurity Costs
- How to Determine Your Company’s Cybersecurity Budget?
- Final Thoughts
We are in a new world of the remote workforce and emerging technologies; most business data is now stored online, making cybersecurity a must-have for all companies.
With regular news of cyberattacks on businesses of all sizes, small businesses are starting to wonder about the risks they face and whether they’re doing enough to protect their companies.
As with many core business functions, cybersecurity often requires a monetary investment and therefore needs space on the budget. The need for cybersecurity isn’t going away any time soon; it’s becoming more relevant for all businesses. That’s why it’s important to consider cybersecurity as a business, financial and practical priority in 2022.
What is Cybersecurity?
Cybersecurity protects computer systems and networks from information disclosure, theft of or damage to their hardware, software or electronic data.
Many think that cybersecurity is one single product or technology that keeps your data safe from cyber threats. This is not the reality.
A robust cybersecurity framework requires a layered approach that safeguards your organisation with technologies, people and processes.
Related Article: Is Antivirus Enough to Protect My Data?
10 Most Common Cyber Threats
Cyber threats are like viruses, and cybersecurity is the vaccine. They both come in different forms. To eliminate the security risks, you must implement the appropriate cybersecurity technology. In other words, you must know the different types of cyber-attacks to come up with the best solutions. Below are the ten most common cyber threats:

1. Malware
“malicious software”, and it refers to any programme or file that can harm the user or the hardware. Examples of malware include Trojans, viruses, spyware etc.
2. Ransomware
A type of malicious software that locks your data, and a ransome is demanded in the form of cryptocurrency to unlock the file; it often comes in emails.
3. Data Breach
Cybercrime where business data or information is leaked to the dark web or sold to hackers.
4. Phishing
Malicious emails that contain links and attachments infected with malware or ransomware with the purpose of stealing data such as login credentials or banking details.
5. DNS Hijacking
Domain Name Server hijacking redirects your trusted clients to a malicious website or their own server
6. Crypto-jacking
Cybercriminals take over your servers and network to theirs for cryptocurrency which costs business money in lost resources.
7. Insider Threats
Internal risks which employees abuse access to the data and information on company networks.
8. Denial of Service Attacks
Network and servers are overloaded by fraudulent network traffic to bring your website or business offline and you’re unable to service clients.
9. Identity Theft
One tries to obtain financial information of a company or individual personal information and use this data to make unauthorised transactions.
10. Property Theft
Also known as intellectual property theft, this cyber threat involves getting access to ideas or creative expressions from an individual or companies without their permission. Although it usually happens on a smaller scale, companies can suffer repercussions if their ideas are stolen and sold to competitors.
Many small businesses neglect their security procedures mainly because they think that it will cost them a lot. However, the consequences of falling victim to a cyber attack can be detrimental to your brand and reputation and may also result in financial loss.
Related Article: Better Cyber Safe Than Sorry: Don’t Wait till You’re Hacked
5 Contributing Factors to Determine Cybersecurity Costs
To ensure that your organisation is secure, it’s crucial to balance the threat with the business’s risk appetite and your skillset in-house before considering the appropriate technical controls or deciding what kind of external resources are needed to help support you. Industry averages can help determine your budget, the costs will differ according to numerous factors:
-
Industry
The number of online security breaches is on the rise across all industries, and some verticals are more vulnerable to these attacks. Financial institutions, construction firms, healthcare providers, eCommerce and IT companies are amongst the fields that experience the most malicious behaviour.
Companies within the industries are more susceptible because operations involve sensitive information to provide financial gain to an attacker. -
Company Size
Employees and the company software and hardware they use can be used by attackers as entry points to access sensitive data – more employees, more possible opportunities for successful phishing attacks and business email compromise. As a result, larger organisations tend to require more in their cybersecurity spending than smaller businesses.
-
Data Types
Businesses that collect more sensitive data will need additional security layers to ensure they are compliant with industry-standard legal compliance.
For example, medical providers who keep patients’ medical reports, or businesses that store customers’ credit card information, the more sensitive the data is, the higher the cybersecurity expenses will be. -
Utilised Hardware and Software Technologies
The hardware and software your operations use determine the kind of security measure that you have in place. After all, safeguarding your company’s server is different from protecting your website. Your current hardware and software set-up play a role in determining the amount you should allot for cybersecurity costs. The more hardware and software you use, the better security options you should have.
-
On-premises deployment vs. Security-as-a-Service (SECaaS)
The traditional on-premise deployment is often very costly. You need to purchase servers or appliances with databases, software and licences, and let’s not forget the facility and utility needed to ensure the on-premise infrastructure is working well.
SECaaS is a subscription model in which you just need to pay a flat fee based on the unit price, depending on the service that you subscribed to with no other hidden installation or service cost. For example, in Email Security Protection as-a-services, you just need to pay a flat “service fee per user” which includes the technology’s licence. You have the option of choosing based on per month or per annual subscription basis.
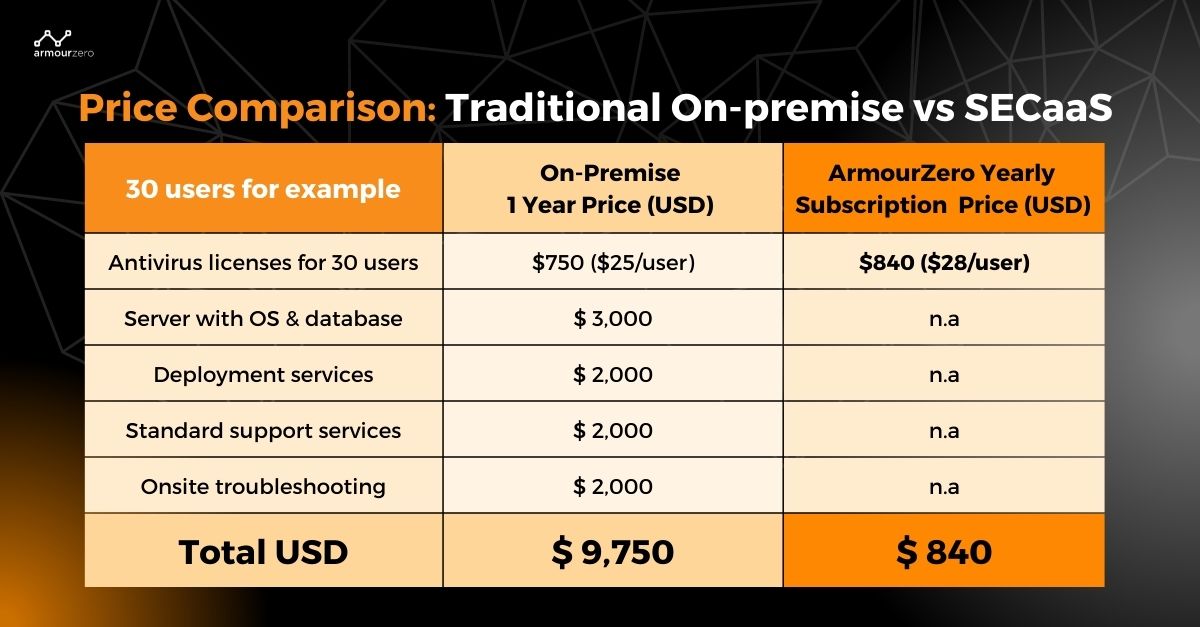
Related Article: What is Security-as-a-Service (SECaaS)? Definition and Benefits
How to Determine Your Company’s Cybersecurity Budget?
The actual amount companies spend on cybersecurity is often tied to their IT budget, your account needs to fit into your business size and risk evaluation. Industry leaders like IBM feel that a healthy cybersecurity budget should make up 9% to 14% of the overall IT department’s annual budget. In reality, the estimates of what companies currently pay vary, ranging from 5.6% to 20% of the company’s total IT spend. Companies in high-tech and finance sectors, naturally, have even bigger budgets.
According to Forbes, spending on cloud security is predicted to increase by 33%, becoming a $585 million-dollar market, and data security will grow by 7.2%.
Big enterprises are doing all in their power to avoid cyber threats, but smaller businesses aren’t far behind. This isn’t a surprise since remote working has left us all exposed. People are much easier targets when out of office, so it’s only logical to increase cybersecurity budgets to avoid being targeted.
Speaking in real numbers: if your 50-employee company has an IT budget of $30,000 annually, you should plan to use at least $3,000 for security. Your cybersecurity provider can often help you identify the highest priority – and lowest cost – solutions to tackle with your limited budget. From there, you can tailor your cybersecurity program and slowly grow your budget in the coming years to provide enhanced protection and help mitigate risks. Just make sure it’s an ongoing program, not a one-time project.
Related Article: What is Security-as-a-Service (SECaaS)? Definition and Benefits
Final Thoughts
Small businesses often operate on a tight budget, and in some cases, the person building and approving the budget may not know the value of cybersecurity. If you’re facing hesitation from the management, performing a basic risk assessment can be a great way to show them where your company stands and how an investment could bolster protection.
The management has a responsibility to guide the company in the right direction, and that includes protecting the company from threats.
Cybersecurity is no longer a “nice to have” – it’s a “need to have” for all businesses. No business can predict when or how they will get a cyber threat, but they can fortify vulnerable systems in advance. A cyber attack can make or break a company depending on how prepared they are.
A comprehensive cybersecurity program doesn’t have to cost a lot of money, but it does require prioritisation and commitment. Look at it this way: Cybersecurity is an investment, not a liability.
Still confused about how to budget for cybersecurity solutions for your company? You can consider ArmourZero, a cybersecurity service subscription fit for your company no matter who and where you are. Also, ArmourZero provides a 1-year free Endpoint Protection with EDR as-a-Service for this service that you can get here.
*This article has been published on e27.co on 26 Apr, 2022
![]()
Written by:
Vivian Wong (VP Marketing at ArmourZero). Digital Marketing expert with vast experiences in marketing field.
Share this post
Related Posts

Earth Day: The Connection of Cybersecurity and Sustainability
- 22 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Uncover the link between Earth Day and Cybersecurity, promoting sustainability through data protection and environmental stewardship. Let’s secure a greener future.

What is DevSecOps? Definition & Best Practices for Tech Industries
- 18 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Learn about DevSecOps, principles, and best practices for the tech industry. Integrate security seamlessly into software development and enhance quality.

Safeguarding Your Organisation During the Hari Raya Holiday
- 09 Apr 2024
- By:Bernadetta Septarini
- Category: ArmourHacks
Protect your organisation from holiday cyberattacks during Hari Raya. Learn more about the risks and best practices for holiday security with ArmourZero.

Cyberattacks: A Growing Threat to Higher Education
- 02 Apr 2024
- By:Fanny Fajarianti
- Category: ArmourHacks
Universities hold sensitive data but face cyberattack risks in the digital age. Explore the impact of cyberattack and learn how to protect your institution.

